1.3: The Dangers of Public Wi-Fi
Essential Questions
- How can you tell the difference between a legitimate public Wi-Fi network and a malicious one set up by an attacker?
- What motivates different types of cyber adversaries, from curious hobbyists to organized criminals?
- How does an "evil twin" attack trick you into connecting to a hostile network?
- What are the key differences between a low-skilled attacker using off-the-shelf tools and a high-skilled one who can create their own?
- Why is simply connecting to an unprotected network risky, even if you don't log into sensitive accounts?
- What simple, practical steps can you take to secure your connection when you have to use public Wi-Fi?
Overview
You meet a friend at your favorite coffee shop, "Sunshine Coffee," to study. As you settle in, your device automatically connects to "Guest Wi-Fi," a network you've used before. Your friend, however, sees a list of available networks and connects to one named "Sunshine Wi-Fi"—it seems plausible enough. A few minutes later, their streaming music cuts out. When they try to log back into the music app, it reports an invalid password. Confused, they ask for your help. A quick look at their settings reveals the problem: they connected to an unprotected network set up by an adversary to trick customers.
This scenario is incredibly common and highlights the hidden dangers of public Wi-Fi. The convenience of free internet access often masks significant security risks. In this case, your friend fell victim to a classic "evil twin" attack. By connecting to the malicious network, all their unencrypted traffic—including their username and password for the music service—was captured by an unseen attacker. The adversary then used those credentials to hijack the account.
This lesson will pull back the curtain on the threats lurking on public wireless networks. You'll learn to think like an adversary, understanding their motivations and skill levels. We will dissect common wireless attacks, such as the evil twin your friend encountered, and explore others like jamming and war driving. Most importantly, you'll learn concrete, actionable strategies to protect yourself, from verifying network legitimacy to using tools like Virtual Private Networks (VPNs) to encrypt your digital life, ensuring your coffee shop study session doesn't turn into a security nightmare.

Identifying the Adversary (1.3.A)
Not all adversaries are created equal. Understanding who might be behind an attack is as important as understanding the attack itself. Their motivations and capabilities vary widely, shaping the kinds of threats you're likely to face. In cybersecurity, we often classify adversaries by their skill level, which helps determine the sophistication of the tools and techniques they employ.
At one end of the spectrum are low-skilled adversaries. These individuals often rely on pre-made, easily accessible tools that exploit well-known vulnerabilities. Think of them as script kiddies who download a program that automates the creation of a malicious Wi-Fi hotspot or scans for open networks. The adversary in the coffee shop scenario was likely low-skilled; they used a common, off-the-shelf tool to set up an evil twin network. Their motivation might be simple curiosity, a desire for bragging rights, or petty theft of online accounts. While they lack the ability to create new attacks or discover unknown flaws, they are still dangerous because the tools they use are effective against unprotected or unaware users.
At the other end are high-skilled adversaries. These are sophisticated actors, often well-funded and part of a larger organization (like a criminal enterprise or a nation-state). They have the technical expertise to create their own custom malware, discover new vulnerabilities (known as zero-day exploits), and adapt their methods to bypass modern security defenses. Their motivations are typically more serious, ranging from large-scale financial fraud and corporate espionage to political disruption. While you are less likely to be the direct target of such an adversary in a coffee shop, the tools and techniques they develop often trickle down, eventually becoming part of the arsenal used by less skilled attackers. Understanding this spectrum helps you appreciate that even a simple-looking attack might be a sign of a more complex threat landscape.
An interactive "Adversary Profile" explorer named "1.3-adversary-profiler". The UI presents cards for different adversary types (e.g., "Script Kiddie," "Hacktivist," "Organized Crime Group," "Nation-State Actor"). Clicking a card reveals a profile with their typical skill level (Low/High), common motivations (e.g., financial gain, political cause, espionage), and examples of attacks they might carry out.
1.3 Adversary Profiler
Script Kiddie
Hacktivist
Organized Crime Group
Nation-State Actor
Common Types of Wireless Cyberattacks (1.3.B)
Public Wi-Fi is a fertile ground for specific types of attacks that exploit the nature of wireless communication. Because radio waves travel through the air, anyone within range can potentially listen in or interfere with the signal. Adversaries have developed several clever techniques to take advantage of this.
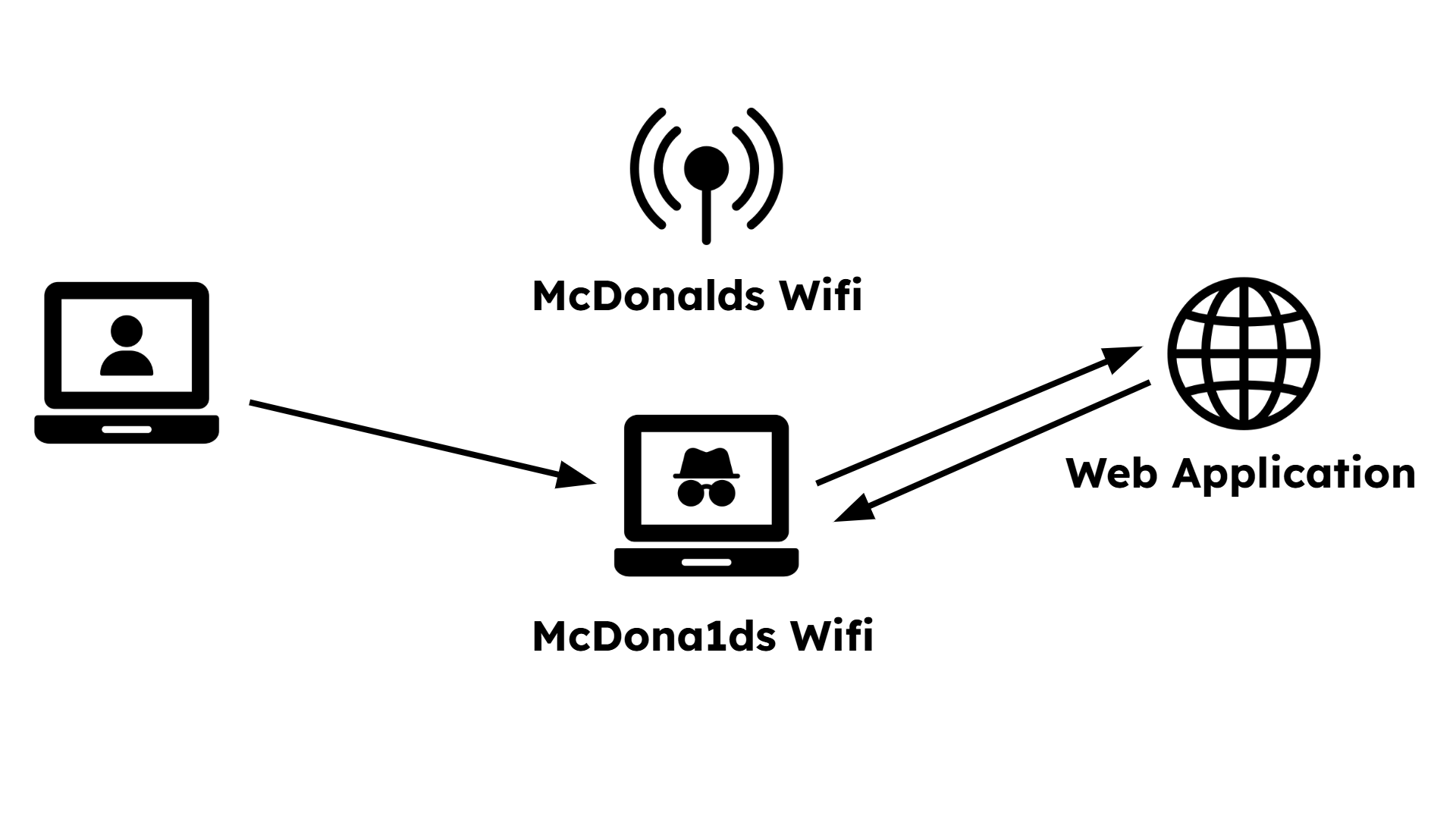
The evil twin attack is one of the most common and effective. As in our opening scenario, the adversary sets up a rogue wireless access point (WAP) with a name, or Service Set Identifier (SSID), that looks legitimate. They might name their network "Starbucks Free Wi-Fi" or, as we saw, "Sunshine Wi-Fi." Unsuspecting users connect, thinking it's the official network. Once you're connected to the evil twin, the adversary is positioned directly in the middle of your internet connection, able to monitor, intercept, or alter all your unencrypted traffic. This is a type of man-in-the-middle (MITM) attack. If you log into a website that doesn't use encryption (HTTPS), they can steal your credentials instantly.
Another type of attack is war driving. This is a reconnaissance technique where an adversary simply moves through an area—driving in a car or even walking with a backpack—using a device to scan for and map out wireless networks. Their goal is to find networks that are unprotected, use weak security protocols (like the outdated WEP or WPA), or have weak passwords. Once they identify a vulnerable target, they can return later to launch a more focused attack. While not an attack in itself, war driving is the information-gathering phase that enables future compromises.
A more disruptive attack is jamming. In this case, the adversary's goal isn't to steal data but to prevent access to the network altogether. They use a device to flood the airwaves with a powerful electromagnetic signal on the same frequency as the legitimate Wi-Fi network. This creates so much interference, or "noise," that your device can no longer communicate with the real access point. This is a form of a denial-of-service (DoS) attack. An attacker might do this simply to cause chaos, or they could use it as part of a more complex attack, perhaps jamming the real network to make their evil twin the only viable connection option.
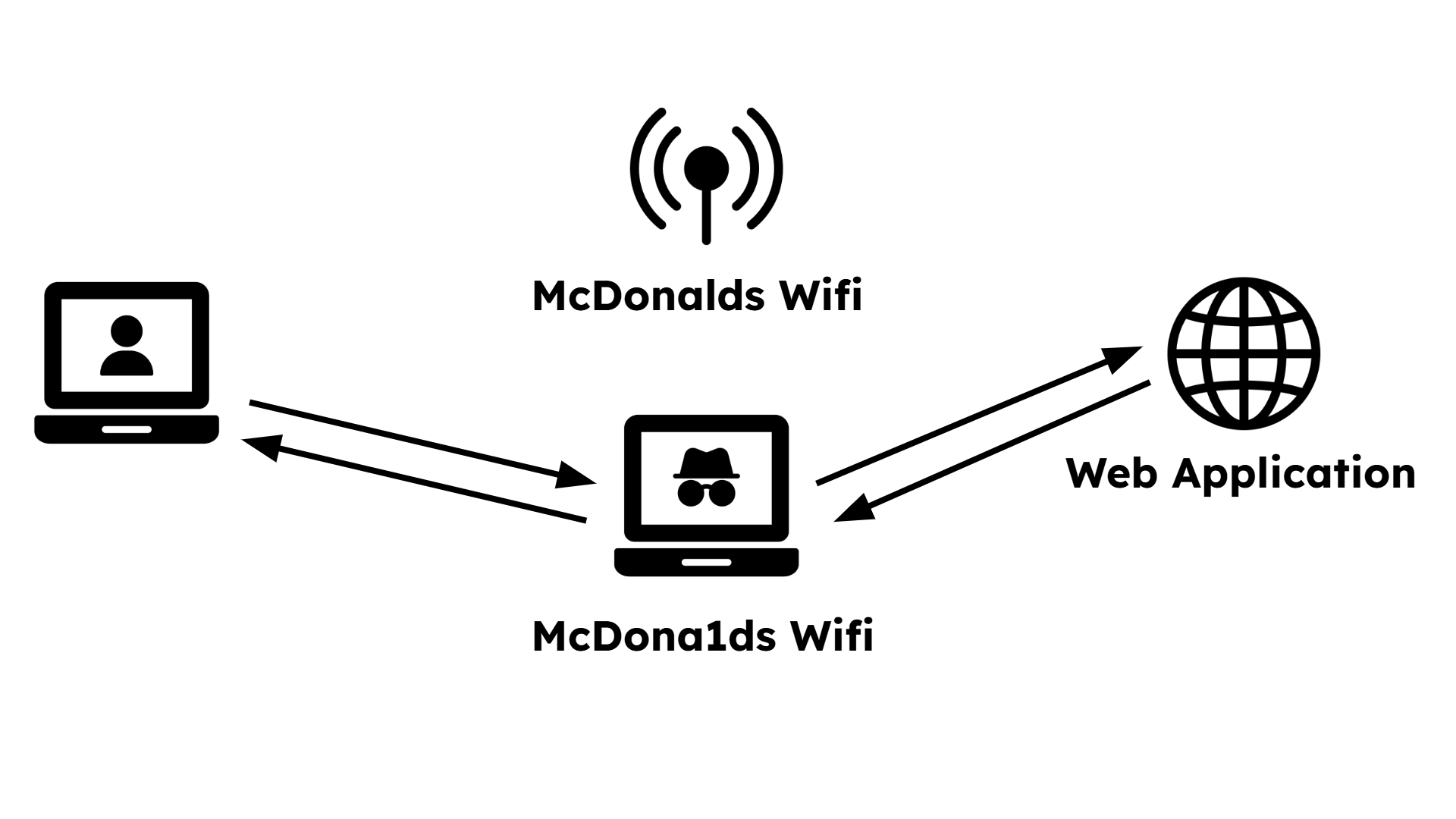
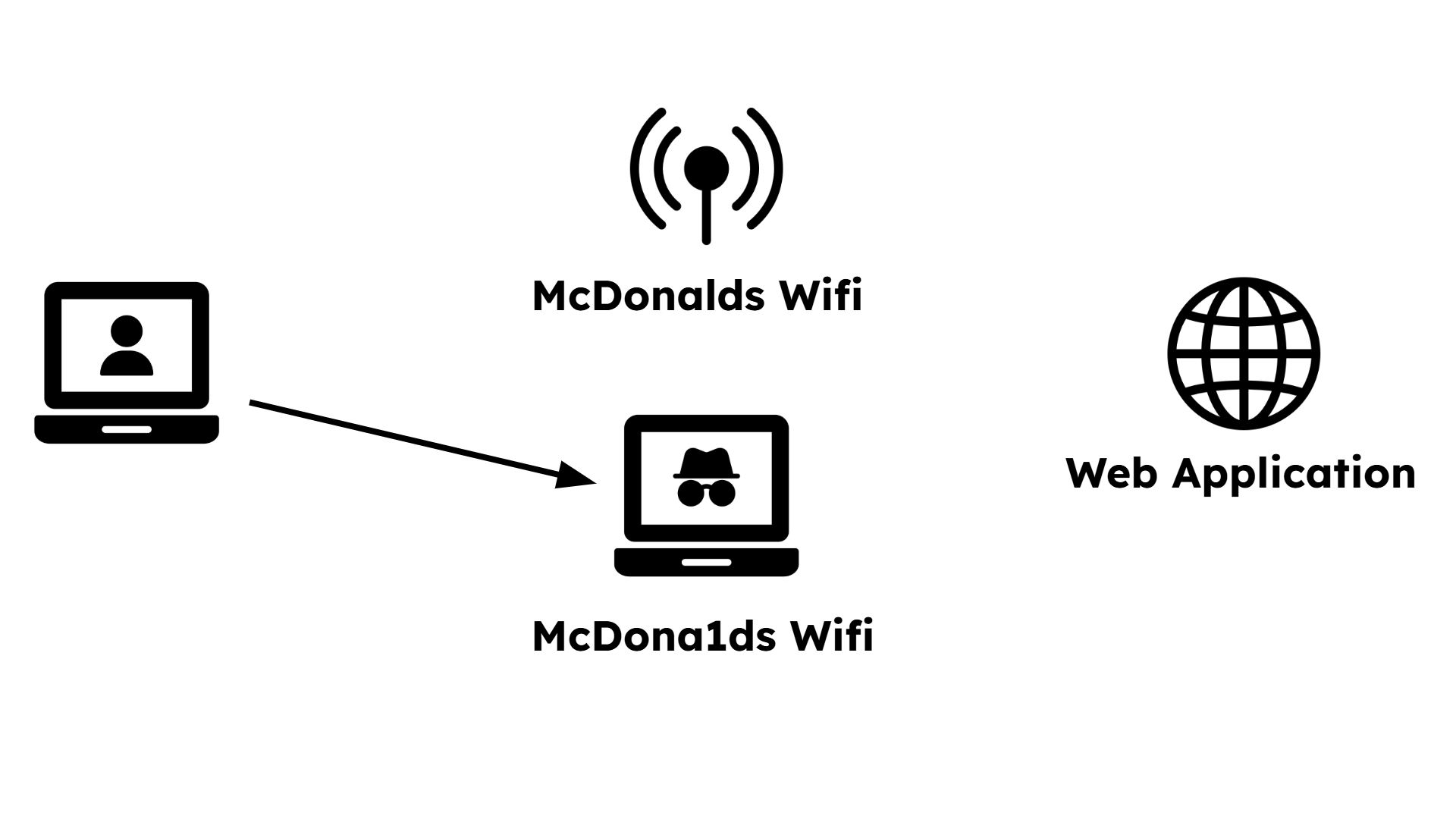
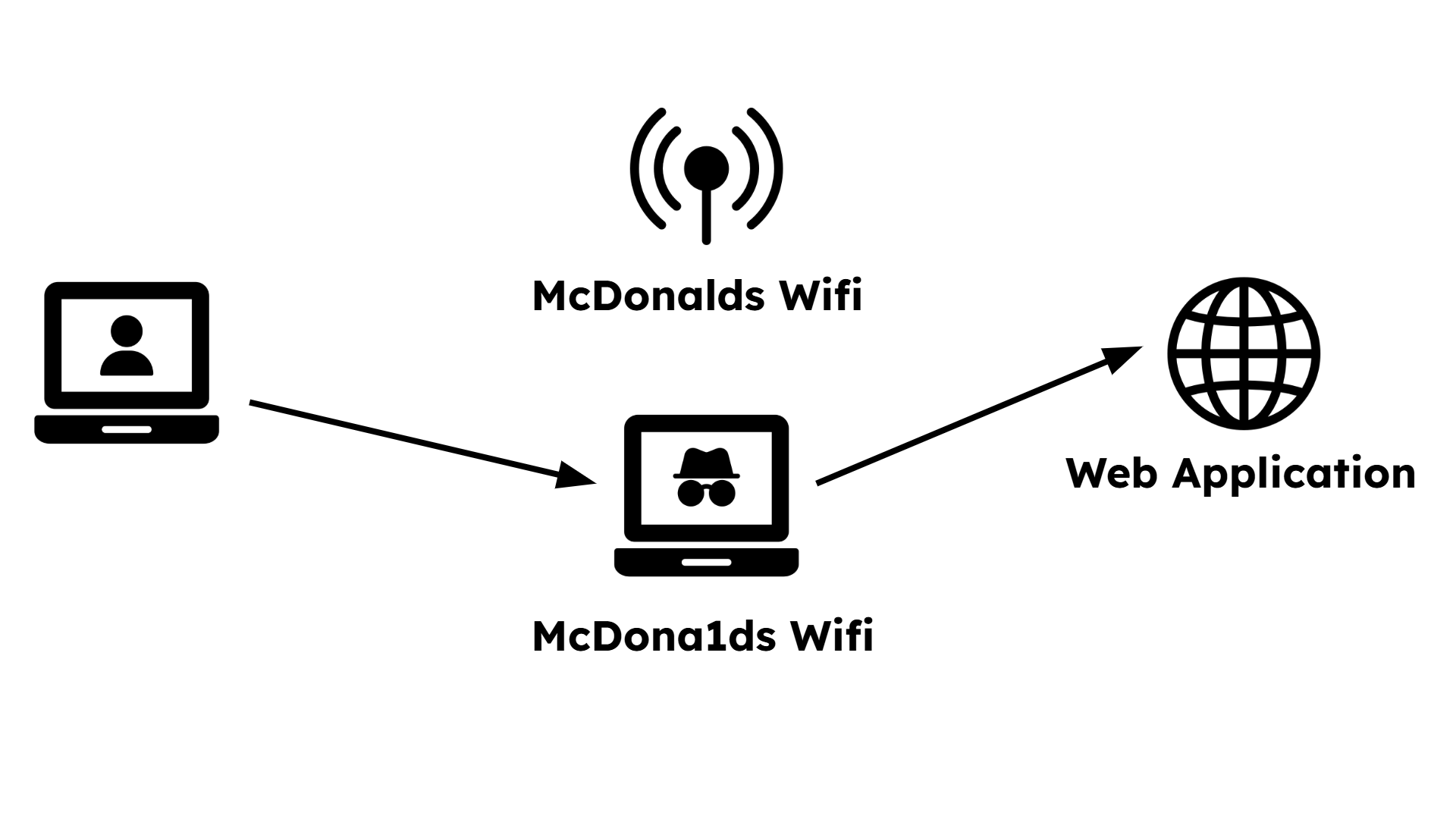
An animated diagram named "1.3-evil-twin-visualizer". Step 1: Show a user's laptop, a legitimate Wi-Fi access point, and the internet (represented as a cloud). A line shows the secure, direct connection. Step 2: An adversary's laptop appears and broadcasts a new, stronger Wi-Fi signal with the same name. Step 3: The user's laptop automatically disconnects from the real access point (AP) and connects to the evil twin. Step 4: The animation shows data (like login credentials) flowing from the user to the adversary, and then from the adversary to the internet, illustrating the man-in-the-middle position.
Step 1
The user, at McDonalds, wants to connect to the Wifi and sees two networks.
How to Protect Yourself from Wireless Attacks (1.3.C)
While the risks of public Wi-Fi are real, you are not powerless. By adopting a few key habits and using the right tools, you can dramatically reduce your vulnerability to these common attacks. The goal is to create layers of security, so that even if one defense fails, others are in place to protect you.
First and foremost, always verify the network name. Before connecting, confirm the exact name of the legitimate Wi-Fi network. Coffee shops and airports often post the official SSID on signs or handouts. If you see multiple similar-looking names, like "Guest Wi-Fi" and "Guest_WiFi_Free," ask an employee which one is correct. A primary defense against an evil twin attack is to simply not connect to it in the first place. As part of this, you should avoid joining unprotected networks. Any network that doesn't require a password should be considered inherently hostile. Without encryption, your data is sent "in the clear," making it trivial for anyone on the network to intercept.
For a powerful layer of protection, use a Virtual Private Network (VPN). A VPN creates an encrypted "tunnel" between your device and a trusted server on the internet. When you connect to a public Wi-Fi network and then activate your VPN, all your internet traffic is routed through this secure tunnel. Even if you accidentally connect to an evil twin, the adversary will only see a stream of scrambled, encrypted data. They won't be able to read your messages, steal your passwords, or see which websites you're visiting. A VPN is one of the single most effective controls for mitigating the risks of untrusted networks.
Finally, ensure your device's software is up to date and that its built-in firewall is enabled. It's also wise to turn off auto-connect or "forget" public networks after you're done using them. This prevents your device from automatically reconnecting to a potentially malicious network with the same name in the future. By combining these practices—vigilance, skepticism, and encryption—you can navigate the world of public Wi-Fi with confidence.

Further Reading & Resources
- FCC: Wi-Fi Security
- Electronic Frontier Foundation (EFF): Choosing the VPN That's Right for You
- NIST: Guidelines for Securing Wireless Local Area Networks (WLANs)
- How-To Geek: What Is an Evil Twin Attack?