3.4: Protecting Networks: Firewalls
Essential Questions
- What is the difference between a stateless and stateful firewall, and when would you use each?
- How do access control lists determine which network traffic is allowed or blocked?
- Why does the order of firewall rules matter, and how can changing rule order affect security?
- Where should firewalls be placed in a network to provide the most effective protection?
- How do next-generation firewalls provide more advanced protection than traditional packet filters?
Overview
Picture your network as a gated community. Every visitor, delivery truck, and resident needs to pass through controlled checkpoints before entering different neighborhoods. Some gates are simple—they check if you're on the approved visitor list. Others are more sophisticated, remembering who you are, tracking your previous visits, and inspecting the contents of your car before letting you through. In the cybersecurity world, these security checkpoints are called firewalls, and they serve as the primary gatekeepers that control what network traffic can flow in and out of your digital neighborhoods.
A firewall is more than just a simple "allow" or "deny" decision maker. Modern firewalls are intelligent systems that can examine packets at multiple layers, track the state of network connections, and even inspect the actual content of communications to detect threats. They operate according to carefully crafted rules—called access control lists (ACLs)—that define exactly what traffic should be permitted or blocked based on factors like source addresses, destination ports, protocols, and even specific applications.
In this lesson, you'll explore the different types of firewalls and understand how each one fits into a comprehensive network defense strategy. You'll learn how to read and write firewall rules, discover why the placement of firewalls within your network architecture is crucial, and master the art of configuring these digital sentries to protect your most valuable assets. By the end, you'll see firewalls not just as barriers, but as intelligent traffic directors that enable secure communication while keeping threats at bay.
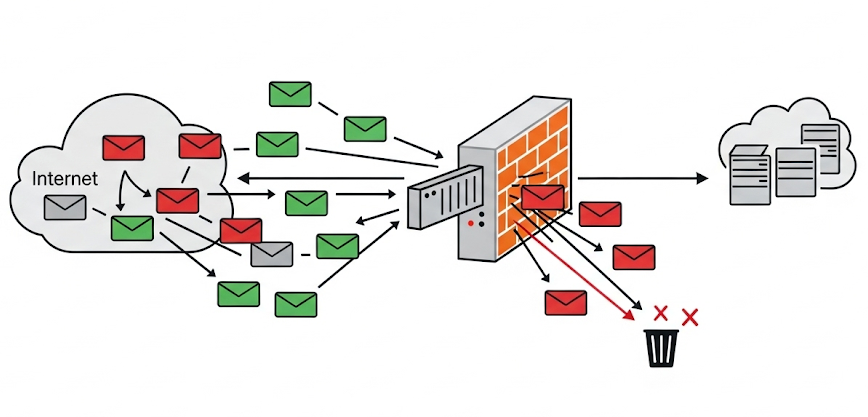
Types of Network-Based Firewalls (3.4.A)
Firewalls have evolved significantly since their inception, growing from simple packet filters to sophisticated systems that can understand and control application-level communications. Understanding the different types helps you choose the right tool for each security challenge.
At the most fundamental level, a firewall is software that controls network traffic by allowing or denying packets based on predetermined rules. This software can run on a dedicated hardware appliance, be integrated into other network devices like routers, or even operate as software on a general-purpose server. Regardless of where it runs, the firewall's job is to examine each packet that tries to cross a network boundary and make a decision: let it through or block it.
Stateless Firewalls
The simplest type is a stateless firewall, which makes decisions based purely on the information contained in individual packet headers. It examines each packet in isolation, looking at factors like the source IP address, destination IP address, source port, destination port, and protocol type. If a packet matches an "allow" rule, it passes through. If it matches a "deny" rule, it's blocked. If it doesn't match any specific rule, it falls to a default action—usually to deny the traffic.
Think of a stateless firewall as a bouncer at a club who only looks at your ID each time you approach. Even if you just walked out for a smoke and are trying to get back in, the bouncer treats you like a complete stranger and checks your ID again. This approach is fast and simple, but it has limitations. For example, if you want to allow web browsing (outbound HTTP requests), you also need to allow the return traffic (inbound HTTP responses). With a stateless firewall, you'd need separate rules for both directions, which can create security gaps.
Stateful Firewalls
A stateful firewall addresses these limitations by tracking the state of network connections. It maintains a connection table that remembers active sessions, including details like which internal host initiated a connection, what external server it's talking to, and what ports are being used. When return traffic arrives, the firewall can check its connection table to see if this traffic is part of an established, legitimate session.
Continuing the bouncer analogy, a stateful firewall is like a bouncer who remembers you left five minutes ago and waves you back in without checking your ID again. More importantly, it can distinguish between legitimate response traffic (someone you actually called) and unsolicited inbound attempts (someone trying to call you without permission). This significantly reduces the number of rules needed and closes many security holes that exist with purely stateless filtering.
Connection Table Example:
+-------------------+-------------------+----------+-------+--------+
| Internal IP | External IP | Int Port | Ext Port | State |
+-------------------+-------------------+----------+-------+--------+
| 192.168.1.50 | 203.0.113.25 | 45678 | 80 | ESTABLISHED |
| 192.168.1.100 | 198.51.100.15 | 34567 | 443 | ESTABLISHED |
+-------------------+-------------------+----------+-------+--------+
Next-Generation Firewalls (NGFWs)
A next-generation firewall (NGFW) takes protection even further by combining traditional stateless and stateful filtering with advanced capabilities. NGFWs can perform deep packet inspection, examining not just packet headers but also the actual content of communications. They can identify specific applications (like Skype, Facebook, or BitTorrent) regardless of what port they're using, detect and block intrusion attempts, and even inspect encrypted traffic metadata for suspicious patterns.
An NGFW is like having a bouncer, a detective, and a content expert all working together at the door. The bouncer checks IDs (traditional filtering), the detective remembers faces and watches for suspicious behavior (stateful inspection), and the content expert can tell if someone is smuggling contraband even if it's hidden in a legitimate-looking package (application awareness and threat detection).
A firewall type comparison tool named "3.4-firewall-comparison". Present three columns representing stateless, stateful, and NGFW firewalls. Show a series of network scenarios (e.g., "Allow web browsing", "Block peer-to-peer applications", "Prevent intrusion attempts") and let learners drag each scenario to the most appropriate firewall type. Provide explanatory feedback on why each firewall type is best suited for particular security requirements.
How Firewalls Use Access Control Lists (3.4.B)
The heart of any firewall is its access control list (ACL)—the rulebook that defines exactly what traffic should be allowed or denied. Understanding how ACLs work is crucial for anyone responsible for network security, as a single misconfigured rule can either create a security vulnerability or block legitimate business traffic.
An ACL is essentially a series of "if-then" statements processed in order from top to bottom. Each rule specifies criteria (the "if" part) and an action (the "then" part). The criteria might include the direction of traffic (inbound or outbound), source and destination IP addresses, port numbers, protocol types, and in advanced firewalls, even application signatures or content patterns. The action is typically either "permit" (allow the traffic) or "deny" (block the traffic).
Here's a simple example of what firewall rules might look like:
Rule 1: PERMIT inbound TCP port 80 from ANY to 192.168.1.10
Rule 2: PERMIT inbound TCP port 443 from ANY to 192.168.1.10
Rule 3: PERMIT outbound TCP port 22 from 192.168.1.0/24 to ANY
Rule 4: DENY inbound TCP ALL from ANY to ANY
Rule 5: DENY outbound TCP ALL from ANY to ANY
This ACL allows external users to access a web server at 192.168.1.10 via HTTP (port 80) and HTTPS (port 443), permits internal users to make SSH connections (port 22) to external servers, but blocks all other TCP traffic in both directions.
The critical aspect of ACL processing is that rules are evaluated sequentially, and the first matching rule determines the action. This means rule order is absolutely crucial. Consider what would happen if we moved Rule 4 (deny all inbound TCP) to the top of the list—suddenly, Rules 1 and 2 would never be evaluated, and no one could access the web server. The firewall would deny all inbound TCP traffic before ever checking if it was destined for the web server.
This sequential processing means that more specific rules should generally come before more general rules. You want to explicitly permit the traffic you need before applying broad denial rules. Many firewall misconfigurations stem from administrators adding rules in the wrong order or not considering how new rules interact with existing ones.
An ACL rule builder and tester named "3.4-acl-configurator". Users can add, remove, and reorder firewall rules using dropdown menus for direction, protocol, ports, and IP addresses. The tool then presents sample network traffic scenarios and shows which rule each packet would match, highlighting how rule order affects the final permit/deny decision. Include a "test traffic" feature where users can input sample packets and see the firewall's decision process step by step.
Effective Firewall Placement in Networks (3.4.C)
Having the best firewall in the world does you no good if it's installed in the wrong place. Effective firewall placement is about understanding your network architecture and positioning these security controls where they can provide maximum protection without unnecessarily hindering legitimate traffic.
The fundamental principle is that every network segment should have firewall protection, especially at boundaries where different security zones meet. At minimum, you need firewalls at every point where your internal network connects to external networks like the internet. This creates a security perimeter that controls all traffic flowing in and out of your organization.
However, a single perimeter firewall is rarely sufficient for modern networks. Consider a typical enterprise network with a DMZ containing public web servers, an internal network with employee workstations, and a high-security zone with database servers containing sensitive customer data. Each of these zones has different security requirements and should be protected accordingly. You'd typically place firewalls between the internet and the DMZ, between the DMZ and the internal network, and between the internal network and the high-security zone.
This layered approach serves multiple purposes. First, it provides defense in depth—if an attacker compromises a web server in the DMZ, they still face additional firewall barriers before reaching critical internal systems. Second, it allows for zone-specific security policies. The firewall protecting the database servers can enforce much stricter rules than the one protecting general employee traffic. Third, it enables lateral movement prevention—an attacker who gains access to one network segment can't easily pivot to attack systems in other segments.
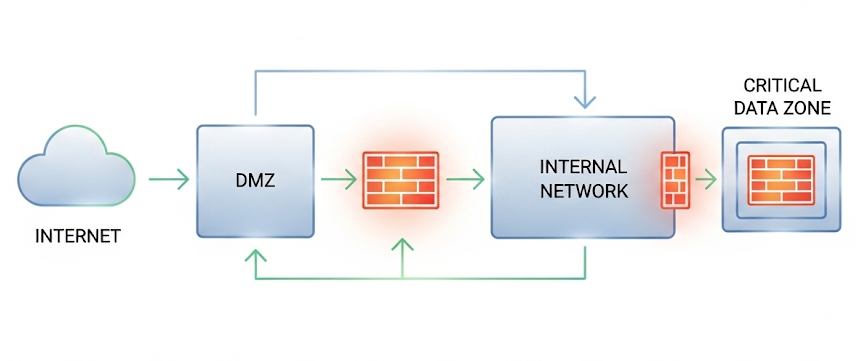
The placement strategy also needs to consider practical factors. Firewalls add some latency to network communications, so you don't want to place them in locations where they'll unnecessarily slow down high-volume, low-risk traffic. Similarly, firewalls require management and monitoring, so they should be positioned where your security team can effectively oversee their operation.
Configuring Firewalls to Manage Network Traffic (3.4.D)
The art of firewall configuration lies in translating business requirements into technical rules that allow necessary traffic while blocking everything else. This process requires understanding both the legitimate communication patterns in your network and the threats you're trying to prevent.
Configuration always starts with requirements gathering. You need to know what services must be accessible, from where, and by whom. For example, your requirements might specify that external customers should be able to reach your web server via HTTPS, your employees should be able to browse the web and check email, and your database servers should only be accessible from your application servers. Each of these requirements becomes the basis for one or more firewall rules.
Let's walk through a practical example. Suppose you're configuring a firewall to protect a small business network. The requirements are:
- External customers must access the web server at 192.168.10.5 via HTTPS
- Employees (192.168.20.0/24) must browse the web and use email
- The database server (192.168.30.10) should only be accessible from the web server
- All other traffic should be blocked
Your ACL might look like this:
# Allow external HTTPS access to web server
Rule 1: PERMIT inbound TCP port 443 from ANY to 192.168.10.5
# Allow web server to access database
Rule 2: PERMIT inbound TCP port 3306 from 192.168.10.5 to 192.168.30.10
# Allow employee web browsing
Rule 3: PERMIT outbound TCP port 80 from 192.168.20.0/24 to ANY
Rule 4: PERMIT outbound TCP port 443 from 192.168.20.0/24 to ANY
# Allow employee email
Rule 5: PERMIT outbound TCP port 25 from 192.168.20.0/24 to ANY
Rule 6: PERMIT outbound TCP port 993 from 192.168.20.0/24 to ANY
# Default deny
Rule 7: DENY ALL from ANY to ANY
Notice how the rules are ordered from most specific to most general, with the default deny rule at the end. This ensures that only explicitly permitted traffic is allowed.
Rule precedence matters enormously. If we accidentally placed the "DENY ALL" rule first, none of the other rules would ever be evaluated, and all traffic would be blocked. Similarly, if we had a rule that said "PERMIT TCP from ANY to ANY" before our specific rules, it would allow far more traffic than intended.
Modern firewalls often include logging capabilities, which are crucial for troubleshooting and security monitoring. When you configure rules, you should also specify what gets logged—typically, denied traffic and potentially suspicious allowed traffic. This creates an audit trail that helps you understand what your firewall is protecting against and whether your rules are working as intended.
A firewall rule simulator named "3.4-firewall-simulator". Present a network diagram with multiple zones and a set of business requirements. Users must configure firewall rules to meet the requirements, then test their configuration against various traffic scenarios. The tool should show both allowed and denied traffic, highlight rule conflicts or gaps, and provide scoring based on security effectiveness and operational efficiency. Include common misconfiguration scenarios and their consequences.
Real-Life Example
The 2008 Heartland Payment Systems breach provides a sobering example of what can happen when firewall configurations are inadequate. Attackers were able to penetrate Heartland's network and install malware on systems that processed credit card transactions. While the attack involved multiple failures, one key issue was that the internal network lacked sufficient segmentation and firewall controls.
The payment processing systems were not properly isolated from other network segments, allowing the attackers to move laterally once they gained initial access. Had there been properly configured firewalls between the payment processing zone and other network segments, with rules that only allowed necessary business traffic, the attackers' ability to explore and compromise additional systems would have been severely limited. The incident ultimately resulted in the compromise of over 130 million credit card accounts and serves as a powerful reminder that firewalls are only as effective as their configuration and placement.
Further Reading & Resources
- NIST SP 800-41: Guidelines on Firewalls and Firewall Policy
- Cisco: Access Control Lists (ACLs) Explained
- Palo Alto Networks: Next-Generation Firewall Features
- SANS: Firewall Checklist