5.3: Protecting Stored Data with Cryptography
Essential Questions
- How does encryption transform readable data into unreadable code that protects files even if they're stolen?
- What is the difference between plaintext and ciphertext, and how does a key control the transformation?
- Why do block ciphers like AES process data in fixed chunks rather than one bit at a time?
- How does the size of the keyspace determine how long it would take an attacker to break the encryption?
- What are the practical steps to encrypt and decrypt files using command-line tools like OpenSSL?
Overview
Picture this: you've just finished researching your family history and compiled sensitive documents including birth certificates, social security numbers, and financial records into a folder on your laptop. Tomorrow, you're traveling with that laptop through busy airports and staying in hotels with questionable Wi-Fi. The thought hits you—what happens if someone steals your device or gains access to your files? All that private information would be completely exposed, readable by anyone who opens the folder.
This is where cryptography becomes your digital guardian. Encryption transforms your readable documents into scrambled, meaningless data that looks like random noise to anyone without the proper key. Even if an attacker steals your entire hard drive, they'll find nothing but digital gibberish where your sensitive files used to be. The original information is still there, perfectly preserved, but it's locked behind a mathematical puzzle that would take thousands of years to solve without the key.
In this lesson, you'll explore how encryption algorithms work to protect files at rest, understand the fundamental concepts of plaintext, ciphertext, and keys, and learn to use industry-standard tools like AES to secure your own data. You'll discover why symmetric encryption—where the same key both locks and unlocks information—forms the backbone of modern data protection, from encrypted hard drives to secure messaging apps.

How Encryption Can Be Used to Protect Files (5.3.A)
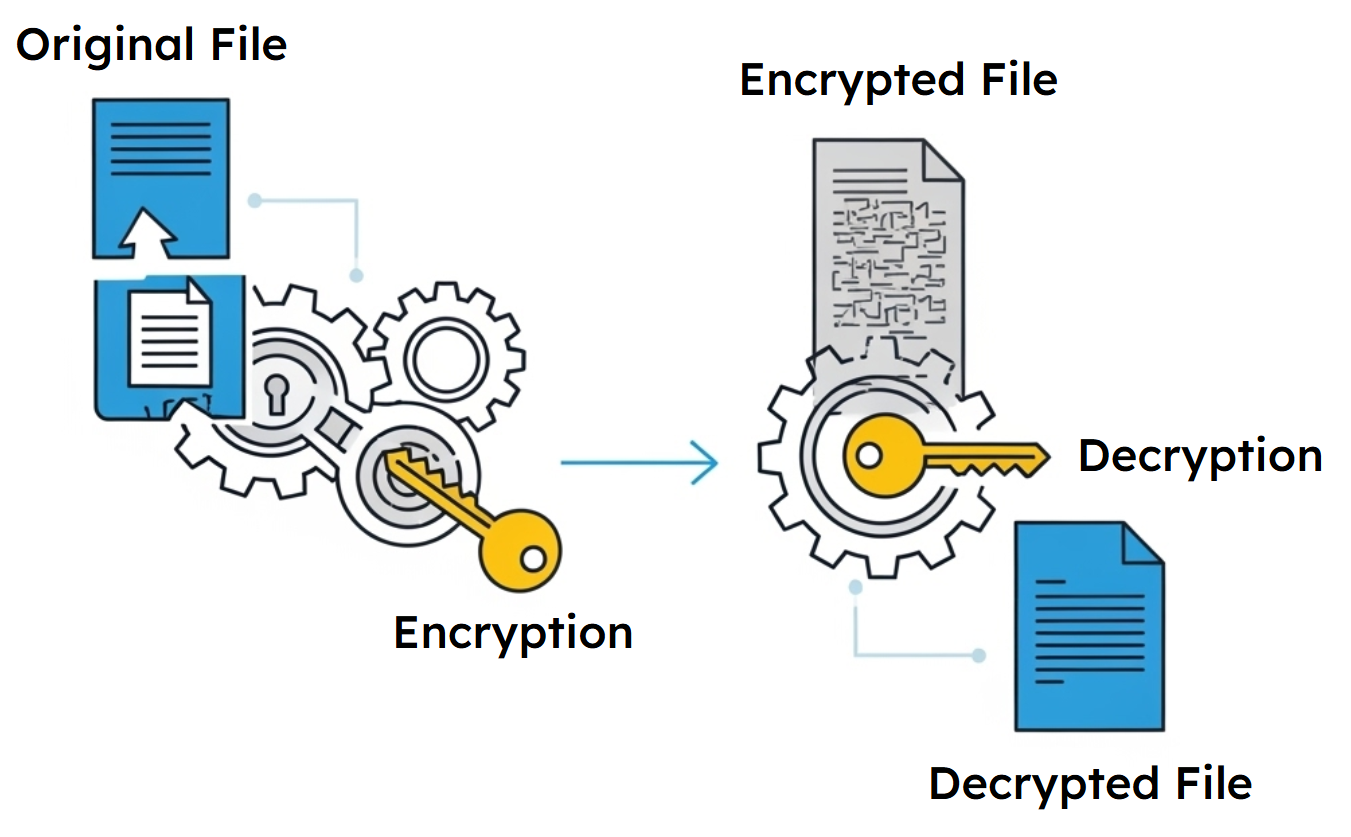
The fundamental purpose of cryptography is to hide information from those who shouldn't see it. When you encrypt a file, you're essentially running it through a mathematical transformation that makes it unreadable to anyone who doesn't possess the correct key. Think of it like translating a document into a secret language that only you and trusted recipients can understand, except the "language" is a complex mathematical algorithm rather than a simple code.
A cryptographic algorithm defines the exact process for this transformation. It specifies how to combine your original information—called plaintext—with a predetermined key to produce scrambled output called ciphertext. The beauty of this system lies in its reversibility: with the correct key, the algorithm can transform the ciphertext back into the original plaintext through a process called decryption.
The security of this entire system depends on the keyspace—the total number of possible keys that could be used with a particular algorithm. If an algorithm uses 128-bit keys, for example, there are 2^128 possible key combinations. That's approximately 340 trillion trillion trillion different keys. Even if an attacker could test one billion keys per second, it would take them longer than the age of the universe to try every possible combination. The larger the keyspace, the longer it takes an adversary to discover the correct key through random guessing.
Cryptographic algorithms fall into two major categories based on their key structure. Symmetric encryption algorithms use the same key for both encryption and decryption—like a house key that both locks and unlocks the front door. Asymmetric encryption algorithms use two different keys: one to encrypt information and a mathematically related but different key to decrypt it. For protecting files at rest, symmetric encryption is typically preferred because it's faster and requires less computational overhead.
A key visualization tool named "5.3-keyspace-calculator". Input: key length in bits (slider from 8 to 256). Output: (1) number of possible keys displayed in scientific notation; (2) estimated time to crack assuming different attack speeds (million, billion, trillion keys per second); (3) visual representation showing exponential growth as bit length increases. Educational goal: demonstrate why longer keys provide dramatically better security.
Cryptographic Key Strength Analyzer
Explore how key length exponentially affects cryptographic security. Adjust the key length to see how the number of possible keys grows and how long it would take attackers to break the encryption using different computational resources.
Key Configuration
Keyspace Size
Exponential Growth Visualization
Brute Force Attack Times
Personal Computer
1 million keys/sec
Gaming Computer
10 million keys/sec
Specialized Hardware
1 billion keys/sec
Supercomputer
1 trillion keys/sec
Distributed Network
1 quadrillion keys/sec
Key Security Insights
Exponential Security Growth
- • Each additional bit doubles the keyspace size
- • Adding 10 bits increases security by 1,024 times
- • 128-bit keys provide 2^128 ≈ 10^38 possibilities
- • Modern computers would need billions of years to break 128-bit keys
Practical Recommendations
- • Minimum 128 bits for symmetric encryption (AES)
- • 256 bits recommended for long-term security
- • Asymmetric keys need to be much longer (2048+ bits for RSA)
- • Consider quantum computing threats for future-proofing
Current Selection Analysis
A 128-bit key provides Strong security. This key length provides strong security suitable for most current applications.
Algorithms also differ in how they process information. Block encryption handles data in fixed-size chunks called blocks, typically 128 bits (16 bytes) at a time. The algorithm takes each block of plaintext, applies the cryptographic transformation using the key, and produces a corresponding block of ciphertext. Stream encryption processes data continuously, one bit or byte at a time, producing output as soon as input arrives. Block ciphers like AES are more common for file encryption because they can handle data of any size by processing it block by block.
The relationship between plaintext, key, and ciphertext forms the foundation of all encryption. Your original data (plaintext) passes through the algorithm along with your secret key, producing scrambled output (ciphertext) that appears random to anyone without the key. When you need to access the data later, you reverse the process: the same algorithm uses the same key to transform the ciphertext back into readable plaintext. This mathematical relationship ensures that encryption and decryption are precise and reliable—there's no guesswork or approximation involved.
Apply Symmetric Encryption Algorithms to Encrypt and Decrypt Data (5.3.B)
The most widely used symmetric encryption algorithm in the world is the Advanced Encryption Standard (AES). If you've ever connected to a WPA3-secured Wi-Fi network, made an online purchase, stored files in cloud storage, or used a smartphone, you've relied on AES encryption. It secures everything from your internet browsing sessions to the contents of your encrypted hard drive, making it the de facto standard for protecting data across virtually every digital platform.
AES is a symmetric key block cipher, meaning it uses the same key for encryption and decryption, and it processes data in fixed-size blocks of 128 bits (16 bytes). One of AES's strengths is its flexibility with key lengths: it can operate with 128-bit, 192-bit, or 256-bit keys. Longer keys create exponentially larger keyspaces and thus provide stronger security, but they also require more computational time to encrypt and decrypt data. For most applications, AES-256 (using 256-bit keys) provides security that's practically unbreakable with current technology.
Understanding AES in practice means knowing how to use the tools that implement it. You have several options for encrypting and decrypting files with AES: command-line interfaces like OpenSSL, specialized software like AES Crypt, or web-based tools for quick experiments. Each approach has its place, but command-line tools like OpenSSL offer the most control and are essential skills for anyone working in cybersecurity.
An AES encryption simulator named "5.3-aes-demo". Features: (1) text input area for plaintext; (2) password input for key derivation; (3) key length selector (128, 192, 256 bits); (4) encrypt/decrypt buttons; (5) output area showing ciphertext in hex format; (6) performance timer showing encryption/decryption speed. Include sample plaintexts like "This is a secret message" to demonstrate the transformation.
Interactive AES Encryption/Decryption Simulator
Experience how AES (Advanced Encryption Standard) transforms plaintext into ciphertext and back. Experiment with different key lengths and observe how the encryption process protects your data.
Input Configuration
Encryption Output
Security Notice
The ciphertext appears random and unreadable. Without the correct password, this data cannot be decrypted, even with knowledge of the AES algorithm.
Key Learning Points:
- • AES is a symmetric cipher - the same key encrypts and decrypts data
- • Longer keys provide exponentially stronger security but slower performance
- • Ciphertext appears random and reveals no information about the plaintext
- • Password strength is critical - weak passwords make strong encryption useless
- • AES-256 is recommended for highly sensitive data and long-term storage
Let's examine how OpenSSL commands work in practice. When you want to encrypt a file called test using AES with a 128-bit key, you use this command:
openssl enc -aes-128-cbc -e -in test -k password -out test.enc
Breaking this down: enc tells OpenSSL to perform encryption or decryption, -aes-128-cbc specifies the algorithm (AES) with key length (128 bits) and mode (CBC, or Cipher Block Chaining), -e indicates encryption, -in test identifies the input file, -k password provides the password from which the encryption key will be derived, and -out test.enc specifies the output file that will contain the encrypted data.
To decrypt that same file, you reverse the process:
openssl enc -aes-128-cbc -d -in test.enc -k password -out test
The only differences are -d for decryption instead of -e for encryption, and the input/output files are swapped. The same password derives the same key, ensuring that decryption reverses the encryption perfectly.
Here's a practical scenario to illustrate the process: imagine you have a file called financial_records.txt containing sensitive banking information. You want to encrypt it before uploading to cloud storage. First, you encrypt:
openssl enc -aes-256-cbc -e -in financial_records.txt -k MySecure2024Pass! -out financial_records.enc
The original readable file gets transformed into financial_records.enc, which contains only random-looking binary data. You can safely upload this encrypted file to any cloud service—even if attackers intercept it, they see only meaningless ciphertext. When you need to access your records later, you download the encrypted file and decrypt it:
openssl enc -aes-256-cbc -d -in financial_records.enc -k MySecure2024Pass! -out financial_records.txt
Your original data emerges intact and readable. The key insight is that the security depends entirely on keeping your password secret. The algorithm and ciphertext can be completely public—in fact, the strength of AES comes from its openness to scrutiny—but the password must remain confidential.
A file encryption workflow demo named "5.3-file-encryption-demo". Simulation of command-line encryption: (1) user selects a sample file type (text document, image, spreadsheet); (2) chooses password; (3) watches simulated command execution with realistic terminal output; (4) sees before/after file comparison (original readable content vs. encrypted binary); (5) can reverse the process with decryption command. Includes common error scenarios like wrong passwords.
Command-Line File Encryption Simulator
Experience realistic file encryption and decryption using OpenSSL commands. Watch how sensitive files are transformed into unreadable ciphertext and restored with the correct password.
Configuration
File Content
Original File: financial_records.txt
CONFIDENTIAL FINANCIAL INFORMATION Bank Account: 123-456-7890 Balance: $45,000.00 SSN: 123-45-6789 Credit Score: 750 This file contains sensitive financial data that should be encrypted before storage or transmission.
Terminal Output
OpenSSL Command Reference
Encryption Commands
openssl enc -aes-256-cbc -e -in file.txt -k password -out file.encEncrypts file.txt using AES-256-CBC with the specified password
openssl enc -aes-256-gcm -e -in data.zip -k secret123 -out data.encUses GCM mode for authenticated encryption (recommended for new applications)
Decryption Commands
openssl enc -aes-256-cbc -d -in file.enc -k password -out file.txtDecrypts file.enc back to the original file.txt
openssl enc -aes-256-gcm -d -in data.enc -k secret123 -out data.zipDecrypts GCM-encrypted files with authentication verification
Security Best Practices
- • Use strong, unique passwords for each encrypted file
- • Prefer AES-256 over AES-128 for sensitive data
- • Consider using GCM mode for authenticated encryption
- • Securely delete original files after encryption
- • Store passwords separately from encrypted files
- • Test decryption before relying on encrypted backups
One important consideration when using OpenSSL is that the encryption key is derived from the password you provide. OpenSSL uses a key derivation function to convert your human-readable password into the binary key that AES actually uses. This means that password strength directly affects encryption security—even with AES-256's massive keyspace, a weak password creates a vulnerable point that attackers can exploit through password-guessing attacks.
The practical implications extend beyond individual file protection. Understanding symmetric encryption prepares you to make informed decisions about disk encryption tools like BitLocker or FileVault, secure communication applications, and enterprise data protection systems. All of these tools rely on the same fundamental principles you've explored: mathematical algorithms, secret keys, and the transformation between plaintext and ciphertext.
Real-World Application
Consider a healthcare organization that needs to protect patient records stored on laptops used by mobile medical staff. Using AES encryption, they can ensure that even if a laptop is lost or stolen, the protected health information (PHI) remains secure and compliant with HIPAA regulations. The same technology protects financial data in banking applications, intellectual property in corporate environments, and personal information in consumer devices. The ubiquity of AES encryption demonstrates how essential symmetric cryptography has become to modern digital security.
Further Reading & Resources
- NIST Special Publication 800-175B: Guideline for Using Cryptographic Standards
- OpenSSL Documentation: Symmetric Encryption
- SANS Institute: Introduction to Cryptography
- AES Crypt: Open Source File Encryption
- Cryptography Engineering by Ferguson, Schneier, and Kohno