4.2: Authentication
Essential Questions
- Why do secure systems never store your actual password, and what mathematical process protects it instead?
- How do adversaries exploit the predictable patterns in human password choices to break into accounts?
- What makes multifactor authentication so much more effective than passwords alone?
- How can you configure login policies that balance security with usability?
- What authentication factors work best in different scenarios and threat environments?
Overview
Picture this scenario: you're a system administrator at a mid-sized company, and during a routine security audit, you discover that a former employee's account is still active and someone has been using it to access sensitive financial data at 3 AM on weekends. The login attempts are coming from overseas IP addresses, but the password being used is correct. How is this possible, and more importantly, how could this have been prevented?
This situation illustrates a fundamental challenge in cybersecurity: authentication—the process of verifying that someone is who they claim to be. Authentication forms the first line of defense for every device, system, and application you use. Whether it's unlocking your smartphone with your fingerprint, entering a complex password into your laptop, or receiving a text message code when logging into your bank account, authentication mechanisms determine who gets access to what.
Understanding authentication means grasping both the mathematical foundations that make it work and the human factors that make it vulnerable. You'll explore how cryptographic hash functions transform passwords into unreadable strings that can verify identity without revealing secrets, why adversaries target the predictable patterns in how people create passwords, and how modern authentication systems layer multiple factors together to create security that's greater than the sum of its parts. By the end of this lesson, you'll know how to configure authentication settings that protect devices while remaining practical for everyday use.
Why Hashes Are Used to Store Passwords (4.2.A)
Why Hashes Are Used to Store Passwords (4.2.A)
When you create a password for any secure system, that system never actually stores your password. Instead, it performs a mathematical transformation called cryptographic hashing that creates a unique digital fingerprint of your password while making it computationally impossible to reverse the process and recover the original password.
A cryptographic hash function takes your password—regardless of whether it's 8 characters or 80—and processes it through a complex mathematical algorithm that produces a fixed-length string of seemingly random characters. This output, called a hash, always looks the same length regardless of the input size. For example, the SHA-256 hash of the password "SecurePass123" produces a 64-character hexadecimal string that looks completely different from the original password. Even the tiniest change to the input—changing "SecurePass123" to "SecurePass124"—produces a completely different hash output.
The beauty of cryptographic hashing lies in its one-way nature. While it's computationally easy to generate a hash from a password, it's mathematically infeasible to work backwards from the hash to determine the original password. This property, called pre-image resistance, means that even if an adversary steals a database full of password hashes, they can't simply read the original passwords.
When you log into a system, the authentication process works by hashing the password you enter and comparing that hash to the stored hash. If the hashes match, the system knows you entered the correct password without ever storing or comparing the actual password text. This process happens so quickly that you don't notice the mathematical complexity occurring behind the scenes.
However, there's one additional security measure that prevents a subtle vulnerability. If two users happened to choose the same password, their hashes would be identical, potentially revealing that fact to anyone who could access the hash database. To prevent this, secure systems add a unique random value called "salt" to each password before hashing it. Each user gets their own salt, ensuring that even identical passwords produce different hashes. The salt is stored alongside the hash, but since it's unique for each user, it effectively eliminates the risk of hash collisions revealing password reuse patterns.
Password Hashing Demonstrator
Explore how cryptographic hashing transforms passwords into secure, irreversible fingerprints. Notice how even tiny changes create completely different hash outputs.
Password Input
Hash Properties
Hash Output
✓ Cannot be reversed to find original password
✓ Different from hash of any other input
✓ Changes completely with any input modification
Why This Matters
How Password Attacks Exploit Vulnerabilities (4.2.B)
Password attacks succeed not because the mathematics of hashing is weak, but because human behavior creates predictable patterns that adversaries can exploit systematically. Understanding these attack methods reveals why individual password choices have far-reaching implications for organizational security.
How Password Attacks Exploit Vulnerabilities (4.2.B)
Password attacks succeed not because the mathematics of hashing is weak, but because human behavior creates predictable patterns that adversaries can exploit systematically. Understanding these attack methods reveals why individual password choices have far-reaching implications for organizational security.
The most direct approach adversaries use involves obtaining credential databases through data breaches or insider threats. Once they possess a collection of password hashes, they can conduct offline attacks using specialized software that tests millions of password combinations per second. These offline attacks are particularly dangerous because they bypass any login attempt limits or account lockout policies—the adversary is working with a copy of the data on their own systems, with no time pressure or detection risk.
Dictionary attacks represent the most efficient offline approach. Rather than randomly guessing passwords, adversaries maintain extensive lists of commonly used passwords gathered from previous breaches, leaked databases, and systematic analysis of human password patterns. These lists often contain millions of real passwords that people have used, organized by frequency and modified with common variations. When an adversary runs a dictionary attack against stolen hashes, they're essentially testing whether any target used a password that someone else has used before—and statistically, many people have.
Brute force attacks take a more comprehensive but slower approach, systematically testing every possible combination of characters up to a certain length. While this method will eventually crack any password given enough time, the computational requirements grow exponentially with password length and complexity. A 6-character password using only lowercase letters might be cracked in minutes, while a 12-character password using the full range of characters could take centuries with current technology.
Online attacks operate differently, targeting live authentication systems rather than stolen databases. Password spraying attacks attempt a small number of very common passwords across many different accounts, staying below the threshold that would trigger account lockouts. This approach exploits organizations where some percentage of users inevitably choose predictable passwords like "Password123" or "Summer2024". Credential stuffing attacks take known username and password combinations from previous breaches and test them against different services, capitalizing on the reality that many people reuse the same credentials across multiple accounts.
The fundamental vulnerability that enables all these attacks is the predictable nature of human-chosen passwords. People tend to use familiar words, meaningful dates, and simple patterns that make sense to them but also make sense to adversaries who understand these patterns.
Password Attack Simulator
Test how different password attack methods would perform against your chosen password. See why password complexity and length matter for security.
Target Configuration
🔍 Tests common passwords and variations from leaked databases
Password Analysis
Enter a password to see analysis
Attack Simulation
Attack Method Details
Security Recommendations
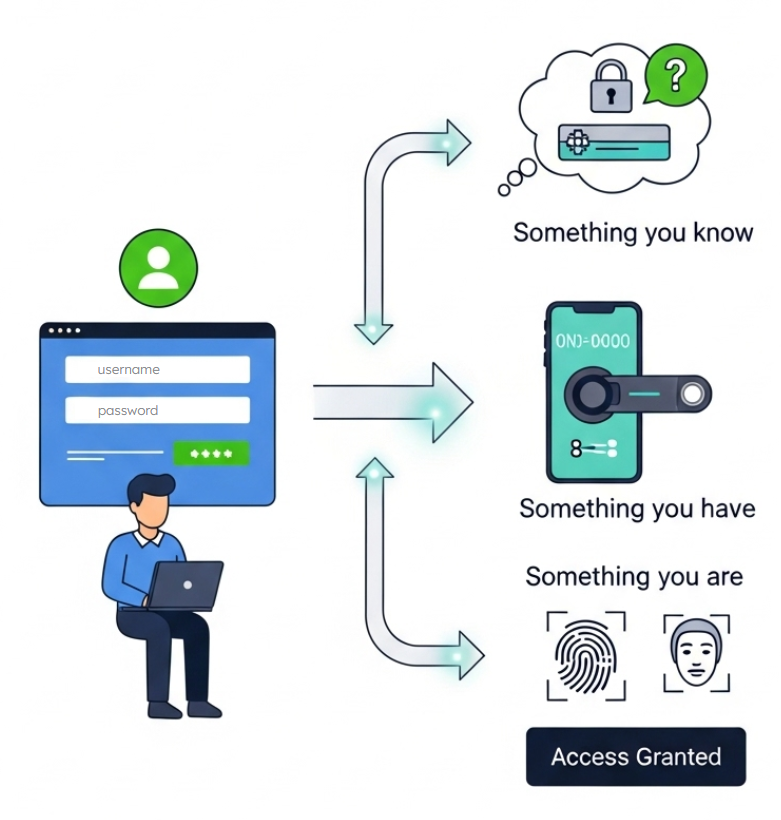
Types of Authentication Factors (4.2.C)
Modern authentication systems move beyond relying solely on passwords by incorporating multiple types of evidence that verify a user's identity. Understanding the different categories of authentication factors—and their respective strengths and limitations—enables you to design authentication systems appropriate for different risk levels and use cases.
Types of Authentication Factors (4.2.C)
Modern authentication systems move beyond relying solely on passwords by incorporating multiple types of evidence that verify a user's identity. Understanding the different categories of authentication factors—and their respective strengths and limitations—enables you to design authentication systems appropriate for different risk levels and use cases.
Knowledge factors represent what a user knows, typically passwords, PINs, or answers to security questions. These factors have the advantage of being entirely digital and requiring no additional hardware, making them convenient and cost-effective to implement. However, knowledge factors suffer from the fundamental weakness that information can be shared, stolen, or guessed. Security questions, in particular, often rely on information that might be publicly available or easy to research about a person.
Possession factors leverage something a user has, such as a smartphone, hardware token, smart card, or key fob. These factors work on the principle that physical objects are much harder for adversaries to obtain remotely than digital information. A hardware token that generates time-based codes creates a possession factor that changes every 30 seconds, making stolen codes useless within a brief window. Smartphones serve as highly effective possession factors because they can receive SMS messages, run authenticator apps, and even perform cryptographic operations.
Biometric factors measure unique physical or behavioral characteristics of the user, including fingerprints, facial recognition, iris scans, voice patterns, or even typing rhythm. These factors offer the compelling advantage of being permanently attached to the user—you can't forget your fingerprint or accidentally share your face with someone else. However, biometric factors face unique challenges: they can't be changed if compromised, they may not work consistently for all users due to injuries or medical conditions, and they require specialized hardware that increases implementation costs.
Location factors determine where a user is attempting to authenticate, using GPS coordinates, IP address geolocation, Wi-Fi network detection, or even time zone analysis. These factors work particularly well for organizations with predictable user locations or specific geographic restrictions. A system might automatically allow access from the corporate office while requiring additional authentication from unusual locations.
The most significant advancement in authentication comes from combining multiple factor types into multifactor authentication (MFA). When a system requires both something you know (password) and something you have (smartphone app), an adversary must successfully compromise both factors simultaneously to gain access. This multiplicative security effect makes MFA dramatically more effective than any single factor alone.
The specific combination of factors matters significantly for both security and usability. Password plus SMS code provides good security against most remote attacks but can be vulnerable to SIM swapping attacks. Password plus hardware token offers excellent security but requires users to carry and maintain additional devices. Biometric plus possession factor eliminates the memorization burden of passwords while providing strong security, but requires more sophisticated infrastructure.
Configuring Secure Login Settings (4.2.D)
Effective authentication configuration requires balancing security requirements with user productivity, creating policies that protect against common attack methods while remaining practical for everyday use. Understanding the impact of each configuration option helps you implement settings that genuinely improve security rather than merely creating the appearance of protection.
Password complexity requirements force users to include characters from multiple categories—uppercase letters, lowercase letters, numbers, and special characters. While this approach does increase the mathematical space an adversary must search during brute force attacks, research has shown that users often respond to complexity requirements in predictable ways. They might capitalize the first letter, add a number at the end, or use simple substitutions like replacing "a" with "@". More effective approaches focus on password length requirements, which provide exponential security benefits while being easier for users to satisfy with memorable passphrases.
Minimum password length requirements provide the most significant security improvement per unit of user inconvenience. Increasing the minimum length from 8 characters to 12 characters makes passwords exponentially harder to crack through brute force methods. However, the implementation must consider the authentication methods being used. Passwords entered frequently on mobile devices might warrant different length requirements than passwords for systems accessed primarily from desktop computers.
Password aging policies require users to change their passwords periodically, typically every 60-120 days. However, modern cybersecurity guidance increasingly questions mandatory password changes because they often lead to weaker overall security. Users faced with frequent password change requirements tend to make minimal modifications to existing passwords, use predictable patterns like adding numbers sequentially, or write passwords down to remember them. Current best practices recommend password changes only when there's evidence of compromise.
Account lockout policies automatically disable accounts after a specified number of failed login attempts, typically 3-10 attempts within a certain time window. These policies provide essential protection against online brute force attacks and password spraying attempts. The lockout duration can be permanent (requiring administrator intervention), temporary (automatically unlocking after a set time), or escalating (increasing lockout duration with repeated violations). Effective lockout policies must balance security protection with legitimate user needs.
The configuration process requires careful consideration of your organization's specific risk profile and user base. High-security environments might justify more restrictive policies despite increased user burden, while consumer-facing systems might prioritize user experience while implementing strong security through other means like multifactor authentication. The most effective approach often involves implementing longer passwords without complex character requirements, enabling MFA where possible, and using intelligent account lockout policies that consider factors like source IP address and time of day.
Authentication Factor Explorer
Explore different authentication factors and their combinations. See how security, convenience, and cost change with different approaches to verifying user identity.
Authentication Factors
Real-World Scenarios
Quick Reference

Real-Life Example
In 2019, a major credential stuffing attack targeted millions of accounts across multiple services, succeeding primarily against accounts that reused passwords from previous data breaches. The attackers used automated tools to test combinations of usernames and passwords leaked from earlier incidents, gaining access to accounts where users had used the same credentials on multiple platforms. Organizations that had implemented multifactor authentication saw dramatically lower compromise rates, even when user passwords were correctly guessed. This incident highlighted how authentication security depends not just on individual password strength, but on systematic approaches that account for human behavior patterns and the interconnected nature of online accounts.
Further Reading & Resources
- NIST Special Publication 800-63B: Digital Identity Guidelines
- OWASP Authentication Cheat Sheet
- Microsoft Security Baseline for Password Policies
- SANS Institute: Password Security Guidelines
- Google Project Zero: Authentication Research