3.3: Protecting Networks: Segmentation
Essential Questions
- How does dividing a network into smaller pieces make it more secure?
- What is the difference between a VLAN and a subnet, and when would you use each?
- Why would an organization place its public web server in a "demilitarized zone" (DMZ)?
- How does network segmentation help contain the damage from a security breach?
- What role does a switch play in creating logically separate networks?
Overview
Imagine a museum with a single, enormous room for all its exhibits. Priceless paintings hang next to interactive science displays, and the historical archives are stored in a corner next to the bustling cafe. If a water pipe bursts in the cafe, it could ruin the archives. If a thief gets into the main hall, every single asset is immediately at risk. This is what a "flat" network looks like—one large, open space where every device can communicate with every other device. A breach in one corner can quickly spread everywhere.
Network segmentation is the practice of being a good museum curator. It's the art of building walls, creating separate galleries, and controlling access between them. Instead of one giant room, you have a gallery for modern art, a secure vault for rare manuscripts, and a separate wing for the noisy, high-traffic cafe. In cybersecurity, these "rooms" are called segments or subnets. By dividing a larger network into these smaller, isolated zones, you can apply specific security policies to each one, limit the spread of attacks, and protect your most critical assets from unrelated threats.
In this lesson, you'll explore the core techniques for carving up a network. You'll learn how firewalls create "demilitarized zones" (DMZs) to safely house public-facing servers, how subnets use IP addressing to create logical divisions, and how VLANs use switches to group devices together regardless of their physical location. More importantly, you'll understand why this separation is one of the most fundamental and effective strategies for building a resilient and defensible network architecture.
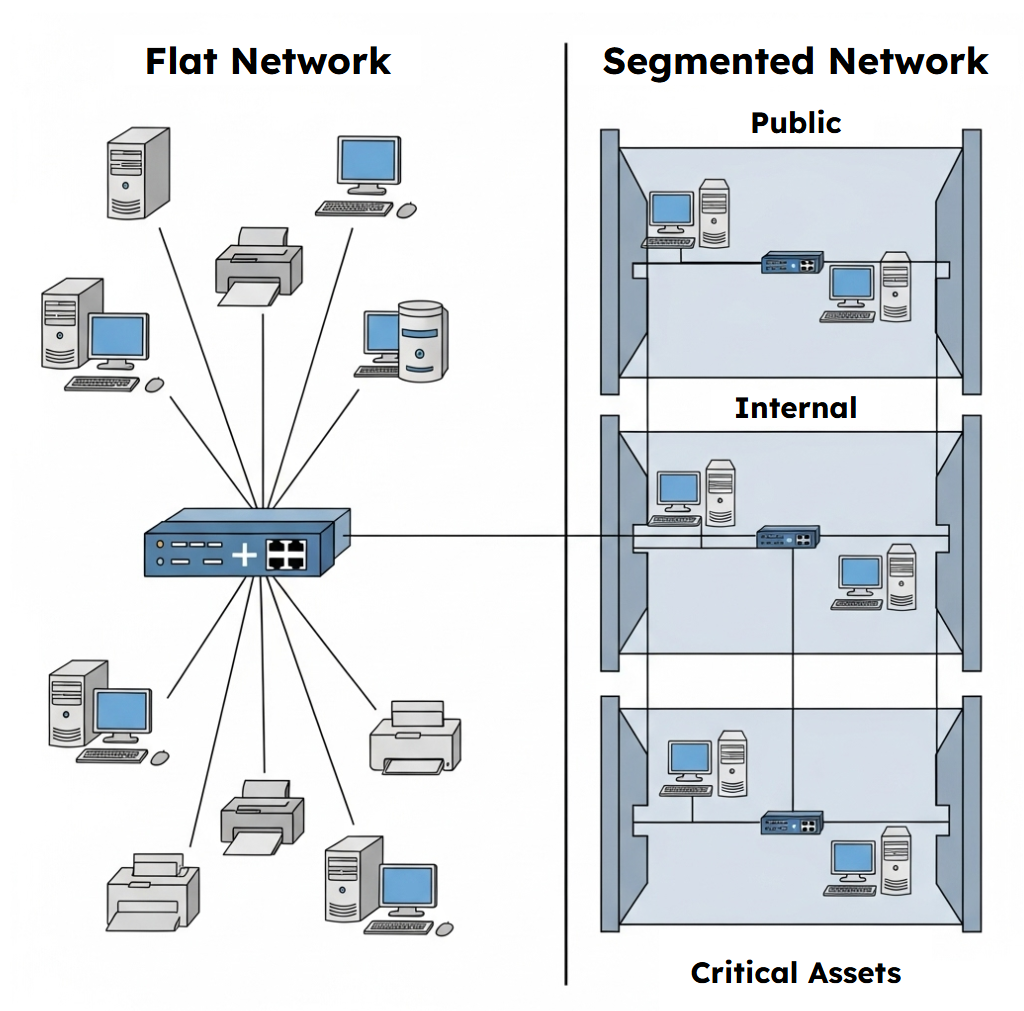
Techniques for Segmenting a Network (3.3.A)
Network segmentation isn't a single technology but a collection of methods that work together to create a layered defense. Each technique offers a different way to draw boundaries within your network, from the broad strokes of separating public and private zones to the fine details of grouping devices by function.
The most common and effective techniques include creating a screened subnet (or DMZ), subnetting with IP addresses, and using Virtual LANs (VLANs) at the switch level.
Screened Subnets (DMZs)
One of the first rules of network defense is to separate what the public can touch from what they absolutely cannot. A screened subnet, more famously known as a demilitarized zone (DMZ), is a special-purpose network segment that sits between your trusted internal network and an untrusted external network, like the internet. It's designed to house servers and services that need to be accessible to the outside world, such as web servers, email servers, or DNS servers.
Think of it as the lobby of a secure building. Visitors can enter the lobby to talk to the receptionist (the web server), but they can't get past the security turnstiles to access the internal offices (the private network). The DMZ is created and enforced by firewalls. A typical setup involves two firewalls: one between the internet and the DMZ, and another between the DMZ and the internal network. This architecture ensures that even if a public-facing server in the DMZ is compromised, the attacker is still trapped in the lobby, blocked by a second firewall from reaching the truly sensitive data inside.
+----------------+ +------------+ +-----------------+ +-----------------+
| The Internet | <=> | Firewall 1 | <=> | DMZ | <=> | Firewall 2 | <=> | Internal Network|
| (Untrusted) | | (External) | | (Web/Email Srv) | | (Internal) | | (Trusted) |
+----------------+ +------------+ +-----------------+ +-----------------+ +-----------------+
Subnetting
While a DMZ separates the entire internal network from the outside, subnetting is a technique used to divide the internal network into smaller, logical pieces. Subnetting works at the IP addressing layer (Layer 3 of the OSI model). A subnet mask is a 32-bit number that splits an IP address into two parts: the network ID and the host ID, identifying the specific network a device is on. By adjusting the subnet mask of an IP address range, a network administrator can create multiple distinct subnets from a single large network block.
For example, a company might create separate subnets for different departments: one for Engineering, one for Finance, and one for Human Resources. Devices in the Engineering subnet can communicate freely with each other, but they cannot directly talk to devices in the Finance subnet. For that, the traffic must pass through a router or a Layer 3 switch, where an access control list (ACL) can be applied to permit or deny the connection. If a malware infection breaks out in the Engineering department, subnetting contains it, preventing it from spreading to the critical financial servers.
A subnet calculator and visualizer named "3.3-subnet-explorer". Input: (1) a base IP address (e.g., 192.168.0.0); (2) a slider to select a subnet mask (from /24 to /28). Output: a visual representation of the network being divided into smaller blocks. The tool should display how many subnets are created, the number of usable IP addresses per subnet, and the IP address range for each one. This helps learners see the direct relationship between the subnet mask and the resulting network segments.
Network Configuration
Network Summary
Binary Visualization
Subnet Details
Subnet 1
254 hostsUnderstanding Subnetting:
Key Concepts:
- • CIDR Notation: /24 means 24 network bits, 8 host bits
- • Network Address: First address in subnet (not usable for hosts)
- • Broadcast Address: Last address in subnet (not usable for hosts)
- • Usable Hosts: Total addresses minus network and broadcast
Security Benefits:
- • Containment: Limit broadcast domains and attack spread
- • Access Control: Apply different policies per subnet
- • Monitoring: Easier to track traffic between segments
- • Performance: Reduce network congestion
Common Subnet Examples:
Virtual LANs (VLANs)
Virtual LANs (VLANs) provide another powerful way to segment a network, but they operate at a different layer—the data link layer (Layer 2). VLANs allow you to group devices into a single broadcast domain, even if they are not physically connected to the same switch. A switch can be configured to assign different ports to different VLANs.
Imagine you have an accounting team spread across three different floors of a building. Physically, their computers plug into different switches. With VLANs, you can configure the switch ports they use to all belong to the "Finance VLAN." As a result, their devices behave as if they were all plugged into the same dedicated switch. Traffic within the Finance VLAN is isolated from all other traffic, such as the "Guest Wi-Fi VLAN" or the "Building-Controls VLAN." This logical separation is incredibly flexible, as you can group devices by function or security level, not just by physical proximity. For traffic to move between VLANs, it must be routed, giving you another point of control.
Why Network Segmentation Increases Security (3.3.B)
The primary goal of network segmentation is to make an attacker's job as difficult as possible. By dividing the network, you introduce multiple barriers that an adversary must overcome, transforming a wide-open field into a maze of locked doors. This strategy enhances security in several key ways.
First and foremost, segmentation contains breaches. When a device is inevitably compromised—whether through a phishing attack, a software vulnerability, or a malicious insider—its ability to cause further harm is limited to its local segment. An attacker who gains control of a workstation in the guest Wi-Fi VLAN cannot immediately pivot to attack the domain controller or the database server in a high-security zone. This containment strategy, often called limiting "lateral movement," is critical for minimizing the impact of an incident. The walls you build with subnets and VLANs act as firebreaks, stopping the security fire from spreading.
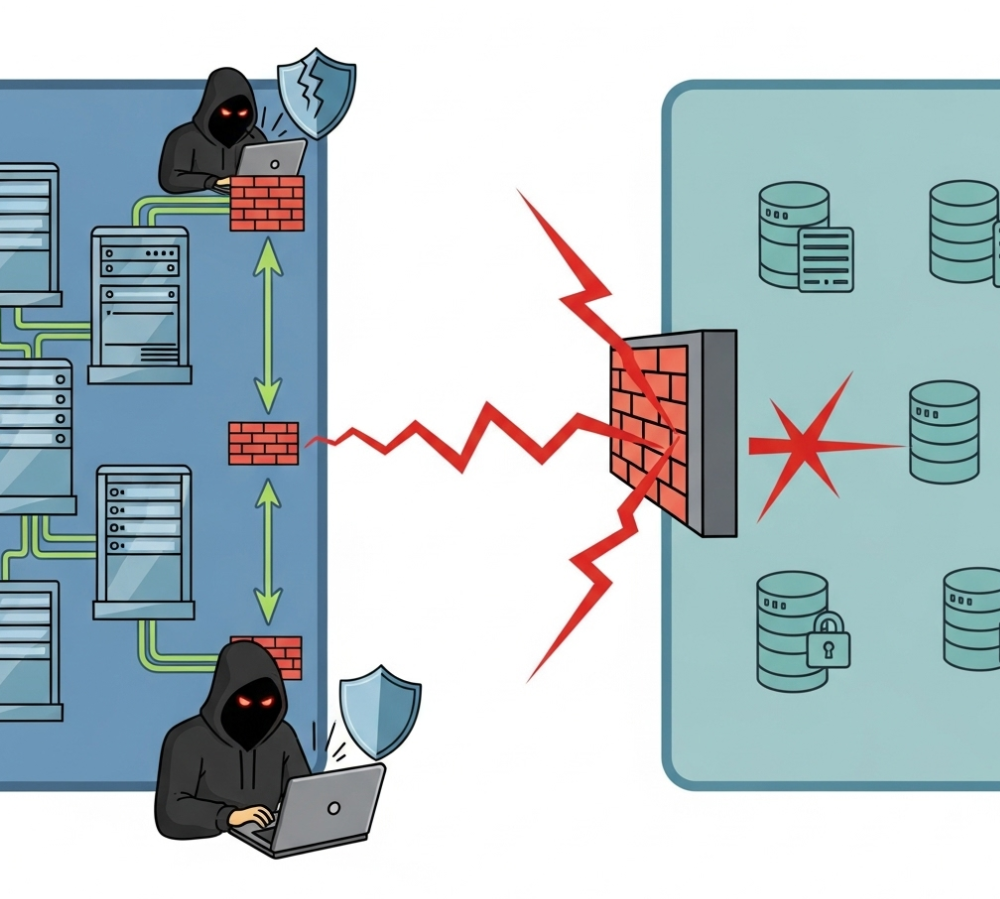
Second, segmentation allows for tailored security policies. Not all data is created equal, and not all network segments require the same level of protection. A public-facing web server in a DMZ has very different security needs than a server storing sensitive patient health records. Segmentation allows you to apply granular security controls where they matter most. You can enforce strict firewall rules and intrusion detection for your critical data segment, while allowing more permissive rules for a less sensitive development environment. This "defense-in-depth" approach concentrates your security resources on protecting your most valuable assets.
Finally, segmentation can improve network performance and monitoring. By breaking up large broadcast domains, VLANs reduce the amount of unnecessary broadcast traffic that each device has to process, leading to a more efficient network. From a security perspective, the reduced "noise" in each segment makes it easier to spot anomalous or malicious traffic. When you're monitoring a small, well-defined subnet, a sudden spike in traffic or a series of unusual connection attempts stands out much more clearly than it would on a massive, chaotic flat network.
Even simple switch features contribute to this. Port security, for instance, can be configured to limit the number of MAC addresses that can connect to a single switch port. This can prevent a MAC flooding attack, where an attacker overwhelms the switch's memory to force it into a "fail-open" mode that broadcasts all traffic. By enabling port security on a per-segment basis, you add another layer of defense right at the edge of the network.
A scenario-based decision tool named "3.3-segmentation-designer". Present a small business network map with several device types (e.g., public web server, employee workstations, file server with sensitive data, guest Wi-Fi access point). The learner must drag and drop these devices into different network zones (DMZ, Internal, Restricted). The tool provides feedback on their choices, explaining why, for example, the web server belongs in the DMZ and why the file server should be in a restricted segment, separate from general workstations.
Design a secure network by placing each device in the appropriate security zone. Consider the security requirements, access needs, and potential risks of each device.
Available Devices
Public Web Server
Hosts company website and customer-facing applications
Employee Workstations
Desktop computers used by employees for daily work
File Server (Sensitive Data)
Contains confidential business documents and financial records
Guest Wi-Fi Access Point
Provides internet access for visitors and contractors
Customer Database
Contains customer personal information and payment data
Email Server
Internal email system for employee communications
Network Printer
Shared printer for document printing and scanning
Backup Server
Stores critical system backups and disaster recovery data
Security Zones
DMZ (Demilitarized Zone)
Public-facing services that need internet access but are isolated from internal networks
Internal Network
Private network for employees and internal business operations
Restricted Zone
High-security area for sensitive data and critical systems
Network Segmentation Principles:
DMZ Zone:
- • Public-facing services
- • Internet accessibility required
- • Isolated from internal network
- • Enhanced monitoring
Internal Zone:
- • Employee resources
- • Business operations
- • Controlled external access
- • Standard security policies
Restricted Zone:
- • Sensitive data systems
- • Critical infrastructure
- • Strict access controls
- • Advanced monitoring
Real-Life Example
The 2013 Target data breach is a classic, if unfortunate, example of what can happen in a poorly segmented network. The attackers initially gained a foothold not by targeting Target's core financial systems, but by compromising a third-party HVAC vendor that had network access. From that initial, low-security entry point, they were able to move laterally across the network, eventually reaching the point-of-sale (POS) systems where they could install malware to scrape customer credit card data.
A more robust segmentation strategy could have prevented this disaster. The HVAC vendor's access should have been restricted to a highly isolated network segment containing only the necessary climate control systems. There was no legitimate reason for traffic to flow from the HVAC segment to the POS segment. Had these zones been properly separated by firewalls and routing rules, the attackers' lateral movement would have been blocked, and the breach could have been contained to a non-critical system. The incident serves as a powerful lesson on how a failure to segment can turn a minor intrusion into a catastrophic data breach affecting millions of customers.
Further Reading & Resources
- NIST SP 800-41, Guidelines on Firewalls and Firewall Policy
- Cisco: What Is a VLAN?
- Palo Alto Networks: What Is Network Segmentation?
- Fortinet: What is a DMZ Network?