3.5: Detecting Network Attacks
Essential Questions
- How do NIDS, NIPS, and SIEM systems work together to create comprehensive network threat detection?
- What are the trade-offs between signature-based and anomaly-based detection methods?
- How can artificial intelligence help security teams manage the overwhelming volume of network data?
- What makes a network traffic pattern suspicious, and how do you distinguish between normal and malicious activity?
- Why do false positives and false negatives represent critical challenges in network security monitoring?
Overview
Picture a busy airport security checkpoint where thousands of passengers pass through every hour. Human guards cannot possibly examine every person and every bag with perfect attention—they would miss threats due to fatigue, distraction, or the sheer volume of people. Instead, the airport uses a combination of automated systems: X-ray machines that flag suspicious objects, metal detectors that beep at metallic threats, and behavioral analysis software that identifies unusual movement patterns. When these systems detect something concerning, they alert human security officers who can investigate further.
Network security operates on the same principle, but the scale is even more staggering. A medium-sized organization's network generates millions of data points every day—every connection attempt, every file transfer, every login, and every packet that flows between systems. No human team, regardless of size or expertise, can manually review all this activity. The solution is automated detection systems that continuously monitor network traffic, analyze patterns, and raise alerts when they spot something that looks like an attack.
This lesson explores the sophisticated tools and techniques used to detect network attacks in real time. You'll learn how Network Intrusion Detection Systems (NIDS) watch traffic for known attack signatures, how Security Information and Event Management (SIEM) systems correlate data from multiple sources to spot complex threats, and how artificial intelligence is transforming the field by identifying subtle patterns that human analysts might miss. Most importantly, you'll develop the skills to analyze network logs and identify the telltale signs of different types of attacks, from ARP poisoning to DNS hijacking.
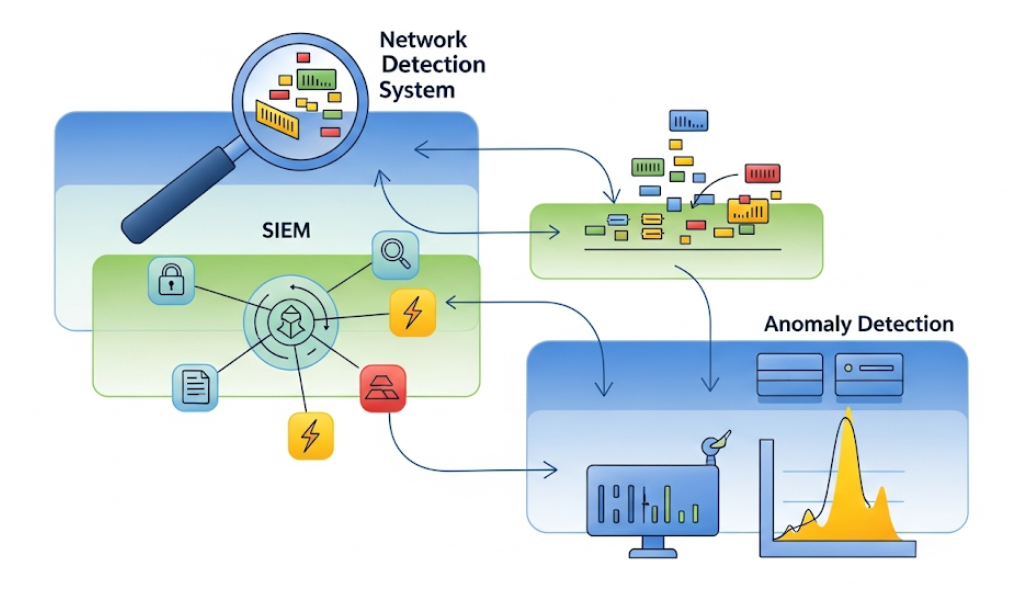
Types of Automated Security Tools (3.5.A)
Modern network security relies on automated tools that process vast amounts of data at machine speed, identifying threats impossible for humans to spot manually. Every day, a medium-sized organization's network generates millions of data points—every connection attempt, file transfer, login, and packet that flows between systems creates a potential clue about malicious activity.
Network Intrusion Detection Systems (NIDS)
A Network Intrusion Detection System (NIDS) monitors packets flowing across network segments, analyzing headers and content to identify patterns matching known attack signatures or suspicious behaviors. Like a security camera watching network traffic, it observes and reports but doesn't interfere with communications. This passive approach ensures that a malfunctioning NIDS won't disrupt legitimate network traffic, but attacks continue while human responders decide how to react.
Strategic placement determines NIDS effectiveness. Organizations deploy multiple sensors at key points: outside the firewall to see incoming threats, inside to catch attacks that slip through, and at network boundaries to detect lateral movement between different organizational segments.
Network Intrusion Prevention Systems (NIPS)
A Network Intrusion Prevention System (NIPS) builds upon NIDS capabilities but adds immediate action against identified threats. Rather than just alerting, a NIPS can block suspicious traffic by closing ports, rejecting packets from specific IP addresses, or temporarily isolating compromised devices.
This active response capability makes NIPS more powerful but riskier. A NIPS misidentifying legitimate traffic as malicious can disrupt business operations. Many organizations deploy NIPS systems in "fail-open" mode, allowing all traffic to pass if the system encounters problems, ensuring security tools don't accidentally cause outages.
Security Information and Event Management (SIEM)
While NIDS and NIPS focus on network traffic, a Security Information and Event Management (SIEM) system correlates data from multiple sources throughout the organization. A SIEM might connect firewall logs, server authentication records, antivirus alerts, and physical access controls to identify complex attack patterns no single system could detect.
The power lies in connecting seemingly unrelated events. A single failed login might not concern anyone, but when the SIEM notices that same username tried against ten servers within five minutes, followed by network scans from the same IP address, it raises an alert for possible brute-force attack. This correlation helps security teams see the bigger picture and identify sophisticated attacks spreading across multiple systems.
3.5 Network Detection System Comparison
Attack Scenario
Attacker systematically probes network services to identify vulnerabilities
NIDS (Network Intrusion Detection)
Key Capabilities:
- • Passive monitoring
- • Pattern recognition
- • Alert generation
- • Forensic analysis
Evidence Collected:
- • TCP SYN packets to multiple sequential ports
- • High connection attempt rate from single source
- • Pattern matches known reconnaissance behavior
NIPS (Network Intrusion Prevention)
Key Capabilities:
- • Active blocking
- • Real-time response
- • Traffic filtering
- • Automatic mitigation
Evidence Collected:
- • Real-time blocking of malicious IP
- • Traffic flow interruption logs
- • Automatic rule deployment
SIEM (Security Information & Event Management)
Key Capabilities:
- • Log correlation
- • Multi-source analysis
- • Long-term storage
- • Advanced analytics
Evidence Collected:
- • Historical context of similar attacks
- • Correlation with external threat feeds
- • Attack attribution and campaign analysis
Detection System Comparison:
NIDS Strengths:
- • Comprehensive network visibility
- • Detailed forensic capabilities
- • No impact on network performance
- • Historical analysis support
NIPS Strengths:
- • Real-time attack prevention
- • Automatic threat response
- • Immediate damage limitation
- • Active network defense
SIEM Strengths:
- • Cross-system correlation
- • Advanced threat analytics
- • Comprehensive incident context
- • Long-term trend analysis
Key Insight:
Each detection system serves a unique role in network security. NIDS provides comprehensive visibility and forensics, NIPS offers immediate threat prevention, and SIEM delivers correlation and strategic analysis. Modern security architectures typically deploy all three systems working together for layered defense.
Leveraging AI to Enhance Threat Detection (3.5.B)
The volume of data generated by modern networks has reached a point where traditional analysis methods are no longer sufficient. A medium-sized organization's network generates millions of log entries daily; large enterprises see tens or hundreds of millions of events. Even with automated filtering, this creates more alerts than human analysts can investigate, leading to "alert fatigue" where security teams become overwhelmed and may ignore potential threats.
AI algorithms can analyze this massive data volume in ways humans cannot. Machine learning systems examine patterns across millions of network events, identifying subtle correlations and anomalies invisible to human analysts. They process data in real time, providing immediate alerts about potential threats rather than discovering attacks days or weeks later.
However, AI threat detection is inherently probabilistic. Rather than definitive answers, AI systems report likelihood percentages—flagging events as "87% likely to be malicious" or patterns as "23% probability of being coordinated attack." This requires organizations to carefully calibrate response thresholds and train security teams to work with uncertainty.
Threshold setting proves crucial for AI-powered detection. Set too high, and the system only alerts on threats it's extremely confident about, potentially missing sophisticated attacks with weaker signals. Set too low, and analysts become overwhelmed by false alarms, potentially missing real threats buried in noise. Organizations must find the balance that maximizes true threat detection while keeping false positives manageable.
AI systems require continuous training and refinement. Attackers constantly evolve their techniques, so models trained on historical data may miss new threats. Organizations need processes to regularly update AI models with new threat intelligence, validate effectiveness against current attack methods, and adjust thresholds based on operational experience.
Detection Presets
Network Events Analysis
Tuning Insights:
Conservative: Higher thresholds reduce false positives but may miss subtle threats
Balanced: Moderate thresholds balance detection and alert fatigue
Aggressive: Lower thresholds catch more threats but generate more false alarms
Optimal Goal: Maximize true positives while minimizing false positives and false negatives
Determining Network Detection Methods (3.5.C)
Choosing the right detection approach requires understanding both your network's characteristics and the threats you're most likely to face. The three main approaches—signature-based, anomaly-based, and hybrid—each have distinct strengths that make them suited to different environments.
Signature-based detection works like virus scanning for network traffic, maintaining a database of known attack patterns and comparing incoming data against this database. This approach is fast, accurate for known threats, and generates very few false positives. It's particularly effective for high-volume networks where processing speed is critical and for detecting well-established attack techniques.
However, signature-based detection has a fundamental limitation: it can only detect attacks it already knows about. New or modified techniques that don't match existing signatures will slip through undetected, making these systems vulnerable to zero-day attacks and sophisticated adversaries who customize their tools.
Anomaly-based detection establishes a baseline of normal network behavior and alerts when activity deviates significantly from this baseline. This method can potentially detect new and unknown attacks because it doesn't rely on predefined signatures. If an attacker uses a novel technique, anomaly-based detection might still catch it because the attack creates unusual traffic patterns.
The effectiveness depends heavily on having consistent network patterns. In predictable environments—such as industrial control systems or dedicated server farms—anomaly-based detection can be extremely effective. However, in dynamic corporate networks with diverse user activities, these systems may struggle to distinguish between legitimate unusual activity and actual attacks.
Hybrid detection combines both approaches, using signatures for known threats and anomaly detection for unknown ones. This provides the broadest protection but increases cost and complexity. Hybrid systems generate more alerts than either approach alone, requiring more sophisticated alert management and larger security teams.
Your choice should consider several factors: network traffic volume and consistency, system criticality, tolerance for false positives, and likelihood of facing novel attacks. High-security environments with critical assets often justify hybrid detection's expense, while smaller organizations with limited resources might focus on signature-based detection for its simplicity and reliability.
Evaluating Detection Method Impact (3.5.D)
The effectiveness of any detection system depends on balancing four critical factors: speed of detection, cost, false positive rate, and false negative rate. Understanding these trade-offs helps you choose the right approach for your specific security requirements and operational constraints.
Speed of detection directly affects your ability to respond before threats cause significant damage. Signature-based systems offer the fastest detection because they simply compare traffic against a database of known patterns, processing at network speeds with minimal latency. Anomaly-based systems are slower because they must perform statistical analysis to determine whether observed behavior deviates from established baselines.
Cost considerations extend beyond initial purchase price. Signature-based systems are generally less expensive to implement and operate, requiring less powerful hardware and simpler management processes. Anomaly-based systems need more processing power for statistical analysis and more skilled staff to configure baseline models. Hybrid systems represent the highest cost option, requiring both types of processing and generating more alerts needing investigation.
False positive rates measure how often detection systems incorrectly identify legitimate activity as malicious. Signature-based systems have very low false positive rates because they only alert on traffic closely matching known attack patterns. Anomaly-based systems have higher false positive rates because they may flag unusual but legitimate activities—such as marketing campaigns generating unexpected website traffic or software updates creating unusual network patterns.
False positives create operational problems: analysts waste time investigating benign events while potentially missing real threats. High false positive rates can lead to "alert fatigue," where security teams become desensitized and may dismiss real threats as false alarms.
False negative rates represent actual attacks that detection systems fail to identify. Signature-based systems are particularly vulnerable when attackers use modified or novel techniques that don't match known signatures. Anomaly-based systems may miss attacks that closely mimic normal behavior or occur gradually over long periods.
False negatives can be catastrophic because they allow attacks to proceed undetected, potentially resulting in data breaches, system compromises, and business disruption. While false positives waste resources, false negatives can threaten organizational survival. This asymmetry means many organizations prefer detection methods with higher false positive rates rather than risk missing real attacks.
Identifying Network Attack Indicators (3.5.E)
Recognizing attack patterns in network logs is a fundamental cybersecurity skill. Each network attack type leaves distinctive traces that trained analysts can spot among millions of daily log entries.
Evil twin attacks create fake wireless access points mimicking legitimate networks to steal user credentials. Detect these by scanning for suspicious SSIDs that closely resemble legitimate networks—"CompanyWiFi" when your real network is "Company_WiFi"—or multiple networks broadcasting the same SSID from different locations. Signal triangulation helps locate unauthorized access points when the same SSID appears from multiple locations simultaneously.
Jamming attacks disrupt wireless communications by flooding radio spectrum with interference. The key indicator is sudden, simultaneous loss of wireless connectivity across multiple devices in a specific physical location while wired connections remain normal. Radio frequency spectrum analyzers can confirm interfering signals and help locate their source.
ARP poisoning attacks exploit Address Resolution Protocol to redirect traffic through an attacker's system. The primary indicator is duplicate MAC addresses in ARP tables—when attackers send false ARP responses claiming their MAC address corresponds to multiple IP addresses. Monitor for unusual ARP traffic spikes, particularly responses without corresponding requests.
MAC flooding attacks overwhelm network switches by sending frames with thousands of fabricated MAC addresses, potentially causing switches to fail into "hub mode" where they broadcast all traffic. Detection involves monitoring for unusual patterns of Ethernet frames with diverse MAC addresses from single sources—legitimate devices typically use one MAC address consistently.
DNS poisoning attacks are difficult to detect because they often target external DNS infrastructure. Indicators include unexplained sudden drops in website traffic when DNS records redirect users to different servers. Monitor DNS query responses for your domain from multiple servers and geographic locations to identify discrepancies suggesting record tampering.
Smurf attacks exploit ICMP traffic by sending ping requests to network broadcast addresses with spoofed source addresses, causing all target network devices to respond simultaneously. The key indicator is sudden spikes in ICMP traffic directed at broadcast addresses—normal operations rarely involve large volumes of broadcast traffic.
Select Attack Scenario to Analyze
Network Log Entries
Attack Indicators
Select indicators you observe:
Real-Life Example
The 2020 SolarWinds supply chain attack demonstrates both the power and limitations of network detection systems. The attackers spent months moving laterally through victim networks, using legitimate administrative tools and carefully timing their activities to blend in with normal network traffic. Traditional signature-based detection systems missed the attack because the malicious activities closely resembled legitimate system administration.
However, some organizations with mature anomaly-based detection capabilities did notice unusual patterns. Network monitoring tools detected unexpected data transfers, unusual authentication patterns, and subtle changes in network behavior that didn't match established baselines. The organizations that detected the intrusion earliest were those that combined multiple detection methods, correlated network activity with other security data sources, and had security teams trained to investigate subtle anomalies rather than just obvious attack signatures.
This incident highlights why modern network security requires a combination of detection approaches, human expertise to interpret subtle indicators, and processes to investigate unusual but not obviously malicious network activity.
Further Reading & Resources
- NIST SP 800-94: Guide to Intrusion Detection and Prevention Systems
- SANS: Intrusion Detection FAQ
- Mitre ATT&CK Framework: Network Defense
- Carnegie Mellon CERT: Network Monitoring and Analysis