2.3: Protecting Physical Spaces
Essential Questions
- Why is a "clean desk policy" considered a security control?
- How can a simple privacy screen on a monitor prevent a data breach?
- What is the purpose of an access control vestibule, and how does it stop tailgating?
- When is disabling a USB port a reasonable security measure?
- How do organizations balance the cost of a security control against the risk it mitigates?
- Why is employee training one of the most effective managerial controls?
Overview
Continuing your role on the physical security team at Xtensr Research Labs, you have completed your initial assessment of the newly acquired building. Your risk assessment document is filled with observations: an unlocked server room, exposed USB ports, and a culture of holding doors open for strangers. Now comes the crucial next step: moving from assessment to action. Your manager has asked you to propose a set of security controls to mitigate the risks you identified. It's not enough to just point out the problems; you need to provide cost-effective and practical solutions.
You start by thinking about the "quick wins." What can be done immediately to reduce risk? You consider drafting a new policy for employees and recommending some simple hardware additions. For the unlocked server room, the solution seems obvious: a better lock. But what kind? A simple key, a card reader, or something more advanced? For the exposed USB ports, should you recommend disabling them entirely, or is there a less restrictive option? And how do you address the ingrained employee habit of being politely insecure?
This lesson focuses on the "how" of physical security: the specific controls and strategies used to protect physical spaces. You will explore the critical role of managerial controls, such as security policies and employee training, which shape human behavior. You will also learn to determine appropriate technical and physical controls—from fences and locks to uninterruptible power supplies (UPS)—to create a robust, layered defense. The goal is to learn how to think like a security professional, selecting and combining controls to build a resilient environment that protects an organization's most valuable assets from physical threats.
Identify Managerial Controls for Physical Security (2.3.A)
While technical controls like locks and cameras are essential, they are often ineffective without strong managerial controls to guide their use and influence employee behavior. Managerial controls are the policies, procedures, and guidelines that form the backbone of an organization's security posture. They are about making security a part of the company culture.
One of the most critical managerial controls is employee security awareness training. You can install the most advanced anti-tailgating turnstile in the world, but if employees don't understand why they shouldn't badge in strangers, the risk remains. Effective training educates employees on common physical threats, such as social engineering tactics like piggybacking, and empowers them to be part of the solution. It teaches them to be vigilant, to question suspicious activity, and to understand their personal responsibility in protecting the organization's assets.
Building on this foundation, organizations should implement a formal workstation security policy. This document outlines the specific rules employees must follow to protect their immediate work environment. Such a policy often includes several key requirements. A clean desk component mandates that sensitive documents, notes, and other materials be properly stored and secured, not left out in the open. A screen lock rule requires employees to lock their computers (e.g., with Windows Key + L or Ctrl + Cmd + Q) whenever they step away from their desk, preventing an opportunistic passerby from gaining access. The policy might also require the use of privacy screen filters on monitors, especially in open-plan offices, to prevent shoulder surfing. Finally, it can mandate the use of surge protectors or even an uninterruptible power supply (UPS) for critical workstations to protect against data loss from power fluctuations or outages.
An interactive "Policy Builder" tool named "2.3-policy-creator". The UI presents a checklist of common workstation security policy items (e.g., "Mandatory screen lock after 2 minutes," "Clean desk at end of day," "Use of privacy screens," "No personal USB devices"). The learner must select the controls they think are most appropriate for different environments (e.g., "Public-facing reception desk" vs. "Secure research lab"). The tool provides feedback on why certain controls are more critical in specific contexts.
Public-facing Reception Desk
Front desk area with high visitor traffic and public access
- • High visitor traffic
- • Public visibility
- • Sensitive visitor information
- • Multiple distractions
Select appropriate security policies:
Automatically locks workstation when idle
All sensitive materials must be secured
Prevents shoulder surfing attacks
Prevents malicious USB attacks
Helps identify unauthorized persons
Prevents unauthorized wandering
Prevents device theft
Provides activity monitoring and deterrence
Determine Mitigation Strategies for Physical Risks (2.3.B)
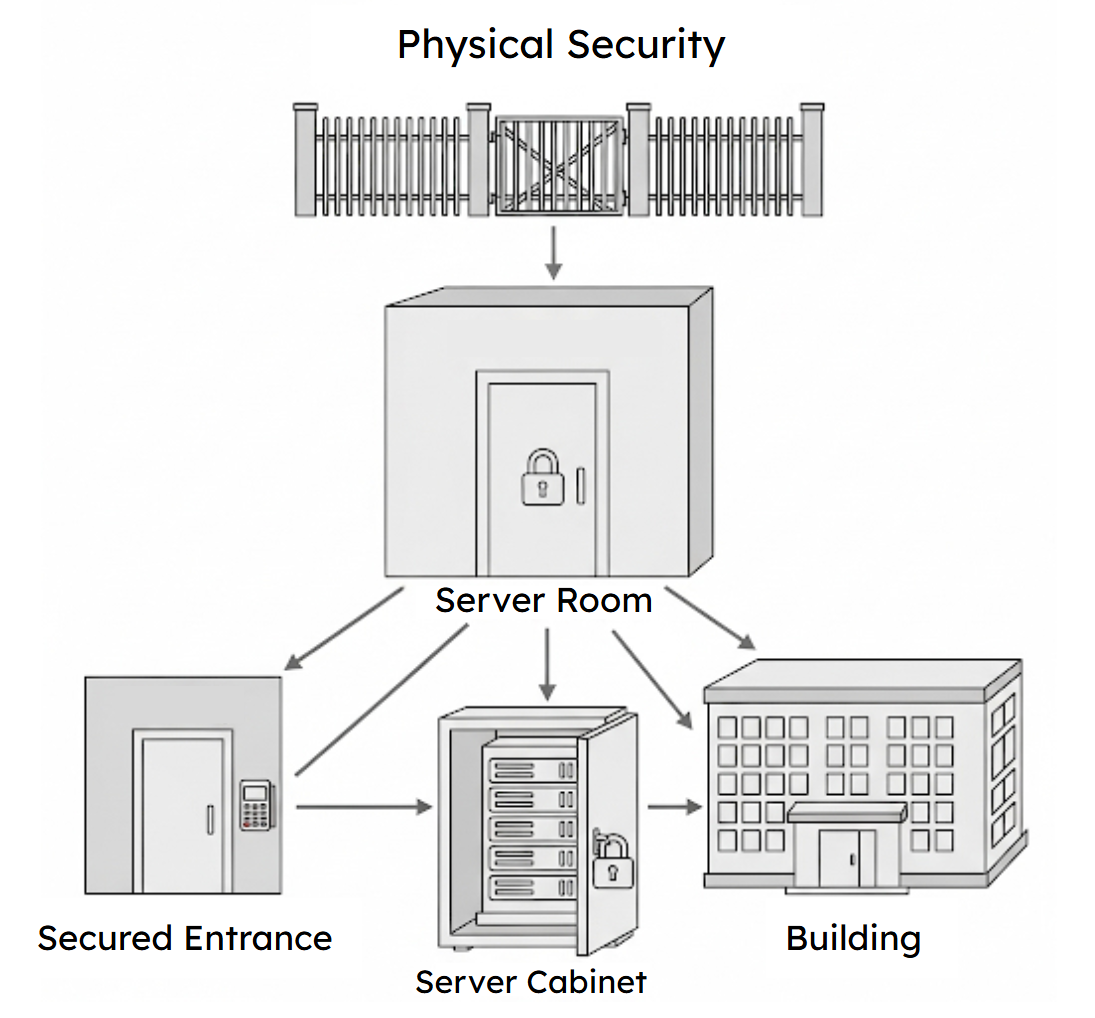
With managerial controls providing the "why," you can then select the right physical and technical controls to provide the "how." The goal is to create a layered defense where each control mitigates a specific risk you identified in your assessment. The selection process involves matching the control to the vulnerability.
To protect the building's perimeter, you can implement controls like fencing, gates, and bollards. These act as a first line of defense, deterring casual intrusion and forcing a more determined adversary to expend time and effort. For entry points, high-quality locks are fundamental. For sensitive areas like a server room, a simple key lock is insufficient. A card reader system is a better choice, as it not only restricts access but also creates a digital log of every entry attempt, providing a valuable audit trail. To combat piggybacking and tailgating, access control vestibules (also known as mantrap doors) are highly effective. These are small, enclosed spaces with two interlocking doors; the first door must close and lock before the second one can be opened, making it physically impossible for more than one person to enter at a time.
Inside the facility, you can mitigate risks to devices directly. To prevent the use of malicious USB drives, an organization can choose to disable USB ports on sensitive workstations through software settings. To protect against data loss or disruption from power outages, critical systems like servers and network equipment should be connected to an uninterruptible power supply (UPS). A UPS is essentially a large battery that provides immediate, temporary power, allowing systems to shut down gracefully or to keep running until a larger backup generator can take over.
Crucially, organizations must prioritize these mitigations based on a cost-benefit analysis. You don't need to install a $10,000 mantrap to protect a low-risk supply closet. The cost of the control should be proportional to the value of the asset it protects and the severity of the risk it mitigates. The risk assessment you completed in the previous lesson is the guide for making these financial and operational decisions.
A "Virtual Security Assessment" scenario named "2.3-security-walkthrough". The UI presents a floor plan of the fictional "Xtensr Labs" with several highlighted vulnerabilities (e.g., "Unlocked server room," "Exposed receptionist PC," "No perimeter fence"). The learner has a budget and a list of available security controls with associated costs. They must "purchase" and place controls on the map to mitigate the identified risks within budget. The tool provides a final score based on how effectively they reduced the overall risk.
Budget Status
Identified Vulnerabilities:
Critical servers are accessible to anyone in the building
Reception computer left logged in with visitor access
Building has no external security barriers
Critical systems vulnerable to power outages
Sensitive documents stored in unlocked filing cabinets
Available Security Controls
Perimeter Fence
$5,000Card Reader System
$3,000Mantrap/Vestibule Doors
$8,000CCTV System
$4,000USB Port Disabling
$500UPS Battery Backup
$2,000Backup Generator
$15,000Motion Detection Sensors
$1,500Security Guard Station
$25,000Secure Document Safe
$1,000Further Reading & Resources
- ASIS International: Physical Security Body of Knowledge
- CSO Online: Layered physical security: The sum is greater than the parts
- How-To Geek: What Is an Uninterruptible Power Supply (UPS)?
- SANS Institute: Securing Workstations