4.3: Protecting Devices
Essential Questions
- How do organizational policies shape device security beyond just technical controls?
- What makes anti-malware software effective at detecting and stopping modern threats?
- Why do software updates represent one of the most critical security practices for any device?
- How can host-based firewalls provide protection even when network security fails?
- What configuration strategies balance security protection with device performance and usability?
Overview
Imagine you're the IT administrator for a growing company, and you've just received an urgent call from the accounting department. Their main workstation is running extremely slowly, pop-up advertisements keep appearing even when no browser is open, and several important files have disappeared from the desktop. When you investigate, you discover that the device hasn't received security updates in six months, the anti-malware software expired two weeks ago, and the host firewall was disabled because it was "blocking a program someone needed to install."
This scenario illustrates why device protection requires more than just installing security software and hoping for the best. Effective device security demands a systematic approach that combines technical controls with organizational policies, user education, and ongoing maintenance practices. A single unprotected device can become the entry point for attacks that spread throughout an entire network Infrastructure.
Device protection operates on the principle of defense in depth—creating multiple layers of security that work together to prevent, detect, and respond to threats. You'll explore how organizational policies establish the foundation for secure device use, how anti-malware software identifies and neutralizes threats, why keeping software updated prevents adversaries from exploiting known vulnerabilities, and how host-based firewalls provide a final line of defense when other controls fail. Understanding these interconnected protections enables you to design comprehensive security strategies that adapt to evolving threat landscapes while supporting productive work.
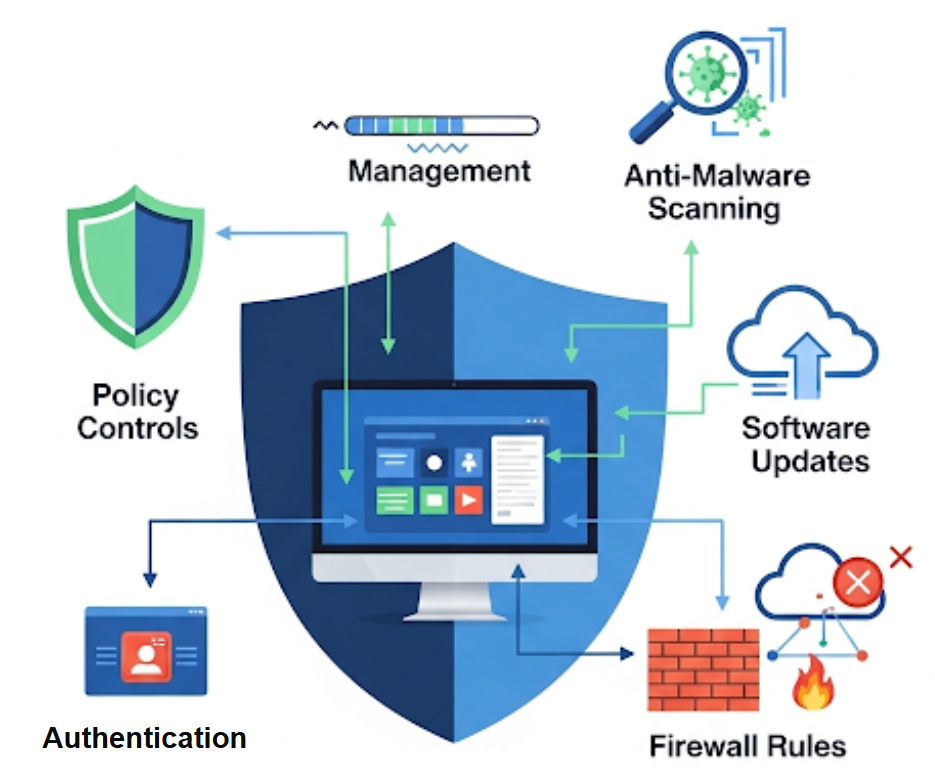
Managerial Controls for Device Security (4.3.A)
Organizational policies form the foundation of effective device security by establishing clear expectations, procedures, and boundaries that guide both technical implementations and user behavior. These managerial controls create consistent security practices across all devices and users, reducing the risk that individual choices will compromise overall security.
Acceptable use policies define the boundaries of appropriate device usage within an organization, specifying both prohibited and required activities. These policies address fundamental questions about device usage: whether employees can access social media sites during work hours, what personal activities are permitted on company equipment, and which websites or applications are considered too risky. Effective policies go beyond simple prohibition lists to explain the reasoning behind restrictions, helping users understand how their choices affect organizational security.
The policy might prohibit access to file-sharing sites not because of productivity concerns, but because these sites frequently serve as malware distribution points. Similarly, restrictions on installing browser extensions reflect the reality that malicious extensions can capture passwords, redirect web traffic, and create persistent backdoors. When users understand the security rationale, they're more likely to follow policies consistently and report potential violations.
Password policies establish organizational standards that go beyond technical authentication system configuration. While login settings determine what the system will accept, password policies guide users in making choices that improve security within those constraints. A comprehensive password policy addresses not just complexity requirements, but also practical guidance about password creation, storage, and management practices.
Modern password policies increasingly emphasize password managers rather than attempting to create memorable passwords meeting complex requirements. The policy might recommend specific password manager applications, provide guidance on securely sharing credentials for team accounts, and establish procedures for handling password-related incidents. These policies also address password reuse, helping users understand why using the same password across multiple systems creates cascading security risks.
Software installation policies control one of the most common vectors for introducing malware and security vulnerabilities. These policies establish clear procedures for how software gets evaluated, approved, and installed on organizational devices. The framework typically includes a pre-approved software list for common business applications, a request process for specialized software needs, and explicit prohibition of certain high-risk application categories.
Software installation policies serve multiple functions beyond preventing malware: ensuring proper licensing and support, reducing attack surface by limiting unnecessary applications, and enabling consistent security configuration across similar installations. When users need specialized software, the policy provides structured evaluation considering security implications, compatibility issues, and ongoing maintenance requirements.
Device Security Policy Builder
Organization Configuration
Policy Impact Assessment
Acceptable Use Policy
- •Devices must be used primarily for authorized business purposes
- •Users are responsible for maintaining device security and reporting incidents
- •Unauthorized access to other users' accounts or data is prohibited
- •Internet access is monitored and filtered for security threats
- •Limited personal use of internet is permitted during breaks
- •Streaming services may be blocked to preserve bandwidth
Password Policy
- •Passwords must be at least 12 characters with mixed case and numbers
- •Password managers are recommended for complex passwords
- •Password changes required every 90 days or after security incidents
- •Previous 6 passwords cannot be reused
Software Installation Policy
- •Software installation requires IT approval and testing
- •Only business-justified software will be approved
- •All software must be from verified publishers
- •Regular audits of installed software will be conducted
How Anti-Malware Software Provides Protection (4.3.B)
Anti-malware software operates as a continuous security guardian for devices, using multiple detection techniques to identify, isolate, and remove malicious software before it can cause damage or establish persistent access. Understanding how these tools work reveals both their strengths and limitations in modern threat environments.
Signature-based detection forms the foundation of most anti-malware systems, maintaining an extensive database of known malware characteristics called signatures. These signatures are digital fingerprints that uniquely identify specific pieces of malicious software based on their code structure, file patterns, or behavioral markers. When scanning a device, anti-malware software compares every file against this signature database, looking for exact or near-exact matches that indicate known threats.
The signature creation process involves security researchers analyzing newly discovered malware to identify unique characteristics distinguishing it from legitimate software. These might include specific byte sequences, unusual file names or locations, registry modifications, or network communication patterns. Once researchers create signatures for new malware variants, they distribute updates to anti-malware products worldwide, typically within hours of discovery.
However, signature-based detection faces significant challenges in modern threat environments. Malware authors actively work to evade signature detection using code obfuscation techniques, polymorphic code that changes appearance while maintaining functionality, and file-less malware operating entirely in system memory. These evasion techniques mean signature-based detection works best against known threats but struggles with novel attacks or sophisticated adversaries.
Heuristic analysis extends anti-malware capabilities by analyzing software behavior rather than just looking for known signatures. This approach examines what programs do rather than what they look like, identifying suspicious activities that might indicate malicious intent. Heuristic engines monitor for behaviors like unauthorized file encryption, attempts to modify system files, suspicious network communications, or efforts to hide processes from administrators.
Real-time protection represents the most critical function of modern anti-malware software, continuously monitoring system activity rather than just performing periodic scans. Real-time engines intercept file operations, network connections, and system modifications as they occur, evaluating each activity for potential threats before allowing it to proceed. This approach prevents malware from executing rather than just detecting it after the fact.
Quarantine and removal functions isolate suspected malware in secure containers where it cannot affect system operations while preserving files for further analysis. When anti-malware software detects a potential threat, it typically moves suspicious files to an encrypted quarantine area, removes references from system startup processes, and logs detailed detection information. This approach allows security administrators to review detections, restore incorrectly identified files, and submit suspicious files for additional analysis.
Anti-Malware Detection Simulator
Simulate different detection methods and see how various malware samples are identified and handled.
The Critical Importance of Software Updates (4.3.C)
Software updates represent one of the most fundamental and effective security practices available to device owners, yet they're often neglected due to convenience concerns or lack of understanding about their security implications. The update process addresses vulnerabilities that adversaries actively exploit, making timely updates essential for maintaining device security.
Vulnerability discovery and disclosure follow a well-established process in the cybersecurity community. Security researchers continuously analyze software for potential security flaws. When they discover vulnerabilities, they typically follow responsible disclosure practices by privately notifying the software vendor and allowing time for patches to be developed before publicly announcing the vulnerability details.
The time between vulnerability discovery and patch availability creates a critical window where systems remain vulnerable. Software vendors prioritize vulnerabilities based on their severity, potential impact, and ease of exploitation. Critical vulnerabilities that allow remote code execution or privilege escalation receive immediate attention, while lower-priority issues might be addressed in regular update cycles.
Zero-day vulnerabilities represent the most dangerous category—vulnerabilities that adversaries discover and exploit before security researchers or software vendors become aware of them. By definition, no patches exist for zero-day vulnerabilities until they're discovered and analyzed. While zero-day attacks receive significant media attention, the vast majority of successful cyberattacks exploit known vulnerabilities for which patches already exist but haven't been applied.
Automated update systems provide the most effective approach for maintaining current security patches while minimizing user burden. These systems can be configured to automatically download and install security updates while requiring manual approval for feature updates that might change system behavior. However, automated updates also introduce risks—a flawed update could simultaneously affect many systems, and automatic restarts might disrupt critical operations at inconvenient times.
Update management strategies vary based on organizational size, risk tolerance, and operational requirements. Large organizations might implement staged deployment processes where updates are first tested on non-critical systems before being rolled out to production environments. Smaller organizations might rely on vendor testing and automated update systems while maintaining backups and rollback procedures in case problems arise.
Configuring Host-Based Firewalls (4.3.D)
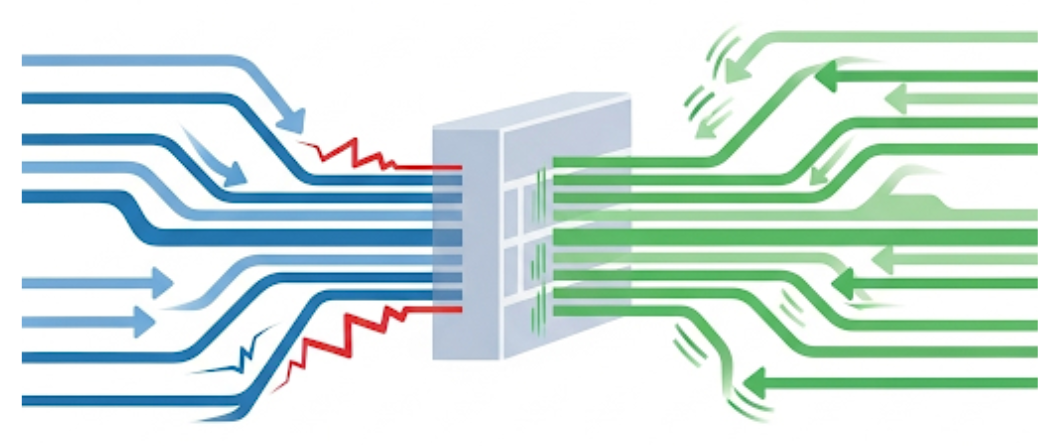
Host-based firewalls provide individualized network security for devices by controlling traffic flowing into and out of specific systems, creating a critical security layer that functions independently of network-level protections. Understanding how to configure these firewalls enables you to create customized security policies that adapt to specific device roles and threat environments.
Host-based firewall architecture operates at the network interface level, intercepting all network traffic before it reaches applications or system services. Unlike network firewalls that protect multiple devices simultaneously, host-based firewalls make security decisions specific to the individual device and its current configuration. This approach provides protection even when devices connect to untrusted networks, travel outside organizational boundaries, or operate in environments where network-level security controls have been compromised.
Rule-based processing forms the core of host-based firewall operation, with the firewall evaluating each network connection against an ordered list of allow and deny rules. The firewall processes rules sequentially, applying the first rule that matches the specific traffic characteristics and ignoring subsequent rules. This sequential processing means that rule ordering significantly affects firewall behavior—a broadly permissive rule early in the list might override more restrictive rules that appear later.
Inbound traffic control blocks unwanted connections from external sources while permitting legitimate network services. Inbound rules typically specify which network ports accept connections, which source IP addresses are permitted or prohibited, and which protocols are allowed through the firewall. For a typical business workstation, inbound rules might permit connections only for essential services like file sharing or remote management tools while blocking all other access attempts.
Outbound traffic control provides equally important protection by preventing compromised systems from communicating with command-and-control servers, exfiltrating data, or spreading to other systems. Outbound rules can prevent malware from establishing remote connections, block access to known malicious domains, and restrict applications to only the network resources they legitimately require.
Application-aware filtering extends basic port and protocol controls by identifying specific applications and services that generate network traffic. Rather than simply allowing or blocking traffic based on port numbers, application-aware firewalls can distinguish between legitimate applications and malware that might use the same network ports, enabling more precise security policies.
The configuration process requires understanding both the device's legitimate network requirements and the potential threats it faces. Different device roles require different firewall configurations—a database server needs different rules than a user workstation, and a device that travels frequently needs different protections than one that remains in a secure network environment. Effective configuration starts with identifying all legitimate network services and applications, then creating rules that permit only necessary traffic.
Host-Based Firewall Configurator
Device Profile
Add New Rule
Firewall Rules (0)
No rules configured
Traffic Testing
Click test to see results
Real-Life Example
In 2017, the WannaCry ransomware attack spread rapidly across global networks, affecting hundreds of thousands of computers in more than 150 countries. The attack exploited a Windows vulnerability for which Microsoft had released a patch two months earlier, but many organizations had not yet applied the update. Devices with up-to-date anti-malware software, current security patches, and properly configured firewalls were largely protected from the attack. However, systems that lacked these basic protections became infected within minutes of network exposure. The incident demonstrated how comprehensive device protection requires coordinated implementation of multiple security controls—no single protection mechanism was sufficient, but the combination of updates, anti-malware, and network controls provided effective defense against this global threat.
Further Reading & Resources
- NIST Cybersecurity Framework: Protect Function
- SANS Institute: Endpoint Security Best Practices
- Microsoft Security Baseline Documentation
- Center for Internet Security (CIS) Controls
- OWASP Mobile Security Project