3.1: Network Vulnerabilities and Attacks
Essential Questions
- How can an attacker trick devices on a network into sending them traffic meant for someone else?
- What happens when a network switch is overwhelmed with fake hardware addresses?
- How can an adversary redirect you to a malicious website even when you type a legitimate URL?
- What are the different ways an attacker can gain access to a supposedly secure local network?
- How do you determine if a network vulnerability is a low, moderate, or high risk?
- Why is leaving a physical network port active in an unsecured area a major risk?
Overview
Imagine you're working at a small clinic. One afternoon, the front desk reports that the patient portal website is down. At the same time, a nurse can't access patient records on the internal file server. The IT team investigates and discovers the network is flooded with an unusual amount of traffic, grinding everything to a halt. It’s not a random outage; it’s a coordinated event. Someone is actively disrupting the network, making it impossible for the clinic to function. This scenario isn't just about a website being unavailable; it's about the fundamental trust and availability of the network itself being compromised.
This lesson dives into the world of network vulnerabilities and attacks. You'll move beyond individual user accounts and social engineering to see how adversaries target the very infrastructure that connects our devices. We will explore how attackers manipulate core networking protocols like ARP and DNS to intercept data or redirect users to fake sites. You'll learn to recognize the signs of common attacks, from the noisy flood of a denial-of-service attack to the silent threat of a rogue access point plugged into an forgotten wall jack. By the end, you will be able to assess network weaknesses and understand how they create tangible risks to an organization's data and operations.
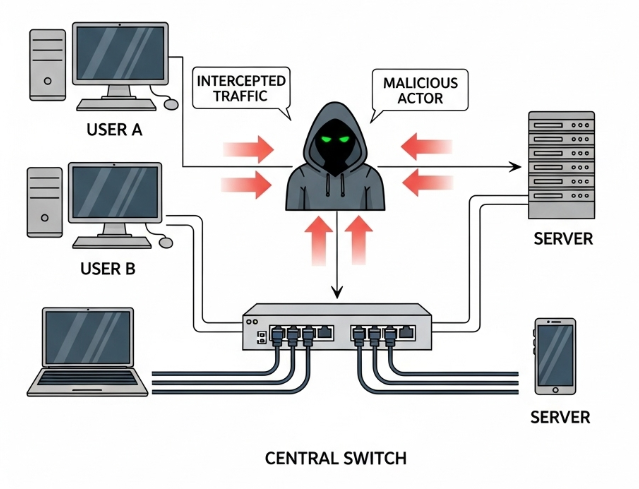
Identify Common Network Attacks (3.1.A)
Network attacks often work by abusing the protocols that devices use to communicate. These protocols were designed for efficiency and trust within a local network, but that trust can be exploited. Understanding these attacks is the first step toward building effective defenses.
An on-path attack (formerly man-in-the-middle) is a foundational concept where an adversary secretly positions themself between two communicating parties. To both parties, the conversation seems direct and secure. In reality, the attacker is intercepting, reading, and potentially altering all the messages before forwarding them. One of the most common ways to achieve this on a local network is through ARP poisoning. The Address Resolution Protocol (ARP) is like the network's address book, matching a device's logical IP address (like 192.168.1.10) to its physical Media Access Control (MAC) address (a unique hardware ID). In an ARP poisoning attack, the adversary sends forged ARP messages to the network's gateway, falsely linking their own MAC address with the IP address of a target device. The gateway updates its table, and suddenly, all traffic intended for the target gets sent to the attacker first. Faking a MAC address in this way is called MAC spoofing.
Another attack that targets network switches is a MAC flooding attack. A switch learns which MAC address is connected to each of its physical ports to efficiently forward traffic. In a MAC flooding attack, an adversary bombards the switch with a huge number of Ethernet frames, each containing a different, fake source MAC address. The switch's memory table, which stores the MAC-to-port mappings, quickly fills up. Overwhelmed, the switch enters a fail-safe mode where it acts like a simple hub, broadcasting all incoming packets to every port on the network. This allows the attacker, who is also connected to the network, to capture all the traffic, an act of eavesdropping that could expose sensitive data.
Attacks aren't limited to the local network. The Domain Name System (DNS) is the internet's phonebook, translating human-readable domain names (like www.example.com) into IP addresses that computers use. In a DNS poisoning attack, an adversary corrupts a DNS server's records, causing it to return an incorrect IP address. For example, they could redirect traffic intended for a legitimate online banking site to a fraudulent look-alike site they control. When an unsuspecting user enters their login details, the attacker captures them. This is a classic method of credential harvesting.
Finally, some attacks aim not to steal data but to make resources unavailable. A denial-of-service (DoS) attack overwhelms a target with so much traffic that it cannot respond to legitimate requests. A smurf attack is a clever and powerful type of DoS. The attacker sends a large number of Internet Control Message Protocol (ICMP) echo requests (like pings) to a network's broadcast address. The trick is that they spoof the source IP address to be their victim's address. The network then amplifies the attack, as every device on the network replies to the victim, creating a massive flood of traffic that can knock the target offline. When this is done using many attacking devices at once, it becomes a distributed denial-of-service (DDoS) attack.
An interactive diagram named "3.1-arp-poisoning-sim". The diagram shows a simple network with a router, a target user, and an attacker. The learner can click a button "Launch ARP Poisoning". When clicked, an animation shows the attacker sending forged ARP packets to the router. The router's ARP table visually updates to show the attacker's MAC address now associated with the target's IP. Finally, traffic from the router heading to the target is animated to reroute through the attacker first.
Network Topology
Router's ARP Table
Attack Progress
How Adversaries Exploit Network Vulnerabilities (3.1.B)
An adversary doesn't need to invent a new attack if they can find an existing weakness to exploit. Network vulnerabilities often stem from misconfigurations, a lack of security controls, or even physical oversight.
One of the most common entry points is an improperly configured firewall or a network with no firewall at all. This allows an adversary to send malicious traffic directly into the network, mapping its internal structure, identifying vulnerable devices, or launching DoS attacks. Once an attacker compromises a single device, they often use that foothold to move laterally across the local area network (LAN), seeking more valuable targets like file servers or domain controllers.
Physical access is another critical vector. An unused but active network port in a public area like a lobby or conference room is a significant vulnerability. An adversary could physically plug their device into the port and gain immediate access to the internal LAN, bypassing the main firewall entirely. Unless port security (a switch feature that limits which MAC addresses can connect to a port) is enabled, the attacker can launch attacks like MAC flooding or ARP poisoning from inside the trusted zone.
Even more insidiously, an adversary can create a rogue access point. By plugging a small, inconspicuous wireless router into that same unsecured network port, they create their own Wi-Fi network. This rogue AP acts as a bridge to the secure LAN, allowing the attacker to access it wirelessly, perhaps from the comfort of a car in the parking lot. This completely bypasses physical security and perimeter firewalls.
Wireless networks themselves present unique vulnerabilities. If a wireless access point's signal bleeds outside the physical building, an adversary can sit nearby and attempt to capture beacon frames and other signals. This allows them to gather information about the network's name (SSID) and security protocols. If the network uses weak encryption, they can attempt to crack it and begin eavesdropping on all wireless traffic. Networks that don't require strong authentication for users and devices make it even easier for an adversary to join and launch attacks from within.
// Switch Port Security Log
Event: Security Violation
Port: Fa0/18
MAC Address: 00:1B:77:34:55:AA
Timestamp: 2025-07-31 14:22:01
Action: Port Shutdown
--
Event: Security Violation
Port: Fa0/18
MAC Address: 00:1B:77:34:55:AB
Timestamp: 2025-07-31 14:22:01
Action: Port Shutdown
--
Event: Rogue AP Detected
SSID: "Free_Corporate_WiFi"
Source MAC: 0A:1C:57:24:99:BB
Connected to Port: Gi0/5
Timestamp: 2025-07-31 15:03:10
The log snippet above shows two distinct events. First, a security violation on port Fa0/18 indicates a device with an unknown MAC address tried to connect, causing the port to shut down—a successful application of port security. The second event shows the detection of a rogue access point, a clear sign of an attempt to create an unauthorized backdoor into the network.
Assess and Document Risks from Network Vulnerabilities (3.1.C)
Not all vulnerabilities carry the same weight. A professional assesses risk by considering the likelihood of a vulnerability being exploited and the potential impact if it is. This evaluation helps prioritize what to fix first. Network vulnerabilities can threaten confidentiality (keeping data secret), integrity (keeping data accurate), and availability (keeping services running).
Automated vulnerability scanners are tools that can check networks for known weaknesses. They produce reports that list detected vulnerabilities, often assigning a severity level (e.g., Critical, High, Medium, Low) and providing recommendations for mitigation. However, a human must still interpret these results in the context of their specific organization. For example, a vulnerability on a public-facing web server has a much different risk profile than the same vulnerability on an isolated lab machine.
The technical skill required to exploit a vulnerability affects its likelihood. An attack that can be automated with a simple script is far more likely to occur than one that requires a team of expert hackers.
-
High risks are vulnerabilities that are relatively easy to exploit and could have a significant impact. An adversary could capture sensitive traffic, spoof a critical device, or take the entire network offline.
- Illustrative Example: An organization has a single, unsegmented internal network accessible via a wireless network with weak encryption. A server on this network runs the company's proprietary web application. An attacker could easily join the Wi-Fi, intercept sensitive customer data, and access the core application server. The likelihood is high, and the impact is critical.
-
Moderate risks are vulnerabilities that might be harder to exploit or would give an attacker less impactful access, such as the ability to gather information about the network layout.
- Illustrative Example: An organization's external firewall is not configured to block incoming ICMP traffic. An attacker could "ping" various IP addresses to map which ones are live, gathering intelligence for a future attack. This doesn't grant them access, but it helps their reconnaissance.
-
Low risks include vulnerabilities that are very difficult to exploit and would likely have minimal negative impact.
- Illustrative Example: An organization's wireless access points broadcast a beacon frame containing the network name (SSID). While this technically reveals the network's existence, it's a standard part of how Wi-Fi works and is generally considered a very low risk, as an attacker can discover the network through other means anyway.
A risk assessment tool named "3.1-risk-calculator". The learner is presented with three scenarios from the illustrative examples above (unsegmented network, ICMP allowed, SSID broadcast). For each scenario, they use sliders to rate the "Likelihood" (Easy to Hard) and "Impact" (Low to Critical). Based on their settings, the tool displays a risk level (Low, Moderate, High, Critical) on a 2x2 matrix. After submitting their assessment for each, it reveals the canonical answer from the curriculum and provides a short explanation.
Scenario 1 of 3
Unsegmented Internal Network
A mid-sized organization has all their internal systems (employee workstations, servers, IoT devices, and guest Wi-Fi) on a single network segment with no internal firewalls or access controls.
Vulnerability Type:
Network Segmentation
Risk Assessment
Calculated Risk Level:
Risk Assessment Guide:
Likelihood Factors:
- • How easy is it to exploit?
- • Are tools readily available?
- • What skill level is required?
- • How detectable is the attack?
Impact Factors:
- • Data confidentiality breach
- • System availability loss
- • Financial/operational damage
- • Regulatory/reputation impact
Further Reading & Resources
- CIS Controls: Secure Network Infrastructure
- NIST Guide to Enterprise Telework, Remote Access, and Bring Your Own Device (BYOD) Security
- Cloudflare: What is a DDoS Attack?
- Fortinet: What is ARP Poisoning?