3.2: Protecting Networks: Managerial Controls and Wireless Security
Essential Questions
- Why are written security policies a critical first step in securing a network?
- How do rules about remote access and VPN usage protect an organization's internal network?
- What is the difference between hiding a Wi-Fi network's name and truly securing it?
- Why is WPA3 a significant improvement over older wireless security protocols like WPA2?
- How can an organization control its Wi-Fi signal to reduce the risk of outside attacks?
- What is the role of MAC filtering in a layered wireless security strategy?
Overview
Imagine you're a network technician for a company that's just moved into a new office space. Your first task is to set up the corporate Wi-Fi. It’s not as simple as plugging in a router and choosing a password. You have to consider who needs access, what they need to access, and how to keep unauthorized people out. An employee connecting from the office needs different access than a remote employee using a VPN, and a guest in the lobby needs a completely separate, isolated network. Without clear rules and the right technical settings, the network could become a gateway for attackers.
This lesson explores the essential partnership between managerial controls—the written rules of cybersecurity—and the technical configurations that bring those rules to life, especially for wireless networks. You'll learn about the importance of creating formal security policies for routers, switches, and VPNs. These policies act as the blueprint for a secure network. Then, you'll dive into the practical steps of securing a wireless network: choosing the strongest encryption, controlling the signal to prevent eavesdropping from the parking lot, and implementing layers of defense to ensure that only trusted users and devices can connect.

Identify Managerial Controls Related to Network Security (3.2.A)
Before you configure a single device, a secure network begins with clear, documented rules. These managerial controls, or policies, define the "what" and "why" of your security strategy. They provide a consistent framework that guides technical implementation and ensures everyone in the organization understands their responsibilities.
A router security policy is a foundational document that sets the minimum standards for the gateways of your network. It might mandate that all administrative logins to the router must use a centralized authentication server, rather than local accounts that can be easily forgotten or mismanaged. It would also likely require disabling unnecessary and insecure services, like Telnet, which transmits passwords in cleartext. Similarly, a switch security policy governs the devices that connect everything on your local network. This policy would require enabling port security to prevent unauthorized devices from plugging in and demanding the use of MAC filtering to create an allowlist of trusted hardware.
For remote employees, a virtual private network (VPN) policy is crucial. This document specifies who is authorized to connect to the internal network remotely and under what conditions. It should mandate strong authentication, such as multi-factor authentication (MFA), and strictly prohibit split tunneling. Split tunneling allows a user to access a public network (like the internet) and a private corporate network at the same time, which can create a dangerous, unintended bridge between a trusted and untrusted environment.
Finally, a wireless security policy establishes the rules for all Wi-Fi networks. This is one of the most critical policies in a modern organization. It should require the strongest available encryption (like WPA3 with AES) and mandate that users authenticate through a robust system, often using an Extensible Authentication Protocol (EAP) that checks credentials against a central server. This policy ensures a consistent, high standard of security across all wireless access points.
These policies are not just suggestions; they are the enforceable backbone of a defense-in-depth strategy. They turn security from a series of ad-hoc decisions into a deliberate, documented, and auditable program.
A policy-matching interactive named "3.2-policy-matcher". The learner is shown three short scenarios: (1) An employee wants to work from a coffee shop, (2) A new switch is being installed in the server room, (3) A visitor needs internet access in the lobby. They must drag and drop the correct primary policy (VPN Policy, Switch Security Policy, Wireless Security Policy) onto each scenario. The tool provides immediate feedback explaining why each policy is the most relevant.
Match each scenario with the most relevant security policy by dragging and dropping. Consider which policy would be the primary guide for handling each situation.
Available Policies
VPN Policy
Governs secure remote access and encrypted connections over untrusted networks
Switch Security Policy
Defines security configurations for network switches and infrastructure equipment
Wireless Security Policy
Controls wireless network access, guest networks, and Wi-Fi security settings
Instructions:
- • Drag policies from here to the scenarios
- • Consider the primary security concern
- • Look for immediate feedback after each drop
Scenarios
Remote Work Request
An employee wants to work from a coffee shop and access company files and email systems while connected to the coffee shop's public Wi-Fi.
Network Infrastructure Upgrade
The IT team is installing a new managed switch in the server room to expand network capacity for additional servers and storage devices.
Guest Network Access
A business visitor needs internet access in the lobby area to check email and access their company's cloud services during a meeting.
Key Learning Points:
Policy Selection: Different scenarios require different primary policy frameworks, though multiple policies may apply.
Risk Context: Consider the primary risk (remote access, infrastructure security, guest access) when selecting policies.
Defense in Depth: While one policy may be primary, organizations often need multiple policies working together.
Configure Wireless Network Security Features (3.2.B)
With a strong wireless security policy in place, you can now translate those rules into technical configurations on your wireless access points (WAPs). Each setting is a layer in your defense.
A common first thought is to hide the network by disabling the beacon frame, which broadcasts the network's name (SSID). While this stops the network from appearing in a casual list of available Wi-Fi, it does not truly secure it. A determined attacker can still discover the network using specialized tools. Therefore, hiding the SSID is considered a very weak form of "security by obscurity" and is not a substitute for strong encryption.
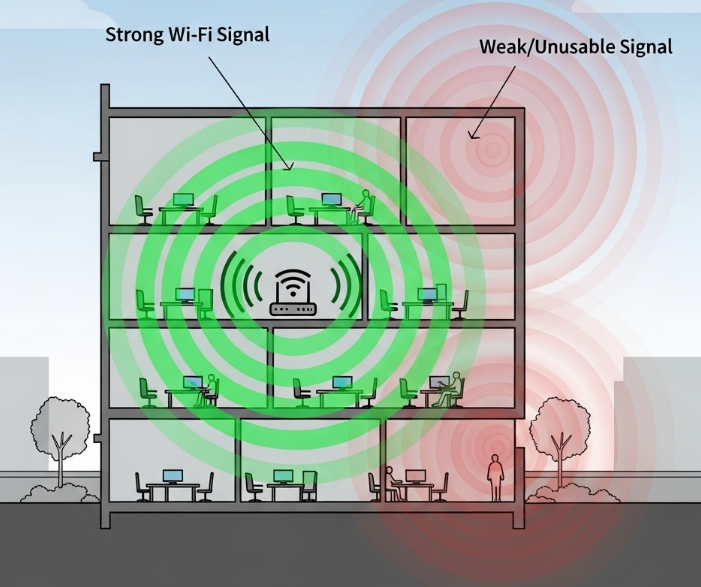
A more effective physical-layer control is managing the WAP's signal strength and direction. You should configure the power levels and antenna placement so the Wi-Fi signal is contained within the physical boundaries of your office. If the signal bleeds strongly into the street or parking lot, it gives an adversary a larger and more convenient area to attempt an attack without having to physically enter the building.
The most critical setting is the wireless encryption protocol. Older standards like WEP, WPA, and WPS have known, severe vulnerabilities and should never be used. The modern standard is WPA3. It offers significant advantages over its predecessor, WPA2. WPA3's protocol, called Simultaneous Authentication of Equals (SAE), protects against offline dictionary attacks by requiring a live interaction for each password guess. This makes it computationally expensive and slow for an attacker to try to crack your password, even if they capture the initial handshake.
// WAP Configuration Snippet
interface wlan0
ssid "Corporate-WiFi"
security_protocol wpa3-enterprise
encryption_suite aes-ccmp
eap_type peap
auth_server 10.1.1.50
mac_filter enabled
mac_list_file /etc/config/authorized_macs.txt
beacon_broadcast enabled
tx_power 50%
The configuration snippet above shows a secure setup. It uses wpa3-enterprise for strong authentication, aes-ccmp for robust encryption, and points to a central authentication server. It also enables mac_filter as an additional layer. MAC filtering allows you to create a list of approved hardware (MAC) addresses. Only devices on this list are allowed to connect. While a sophisticated attacker can spoof a MAC address, this control is effective at stopping casual, unauthorized connection attempts and adds another hurdle for an attacker to overcome.
By combining strong WPA3 encryption, controlled signal strength, and layers like MAC filtering, you build a wireless network that is resilient against a wide range of common attacks.
An interactive WAP configuration panel named "3.2-wap-config-sim". The learner is presented with a simplified wireless access point UI with several choices: Security Protocol (WEP, WPA2, WPA3), SSID Broadcast (Enabled/Disabled), and MAC Filtering (Enabled/Disabled). Their goal is to configure the WAP according to a provided mini-policy ("Maximize security for corporate use"). The tool provides feedback on their choices, explaining why WPA3 is essential, why hiding the SSID is not a primary security feature, and how MAC filtering adds a layer of defense.
Corporate Security Policy
“Maximize security for corporate use while maintaining reliable connectivity for authorized users.”
WAP Configuration Panel
Configuration Analysis
Configure your wireless access point settings and click “Apply Configuration” to see the security analysis.
Further Reading & Resources
- NIST SP 800-153: Guidelines for Securing Wireless Local Area Networks (WLANs)
- Wi-Fi Alliance: WPA3™ Security
- SANS Institute: Top 5 Wi-Fi Security Myths
- How-To Geek: Why You Shouldn't Hide Your Wi-Fi SSID